Why Do We Need More Security In Healthcare Network
Undoubtedly, the Internet of Things (IoT) and related services have revolutionized the healthcare industry. There are many examples for this, i.e. it is possible to directly access patient records, provide remote diagnostics, and provide appropriate treatment options. There are also lifecycle management and apps for monitoring vital signs.
Two motifs are particularly driving growth in this segment. Firstly, the offered services should become more efficient and, secondly, they should offer its users better treatment quality. The so-called “connected health” market has grown so fast that experts predict that it will reach a volume of around 612 billion US dollars by 2024.
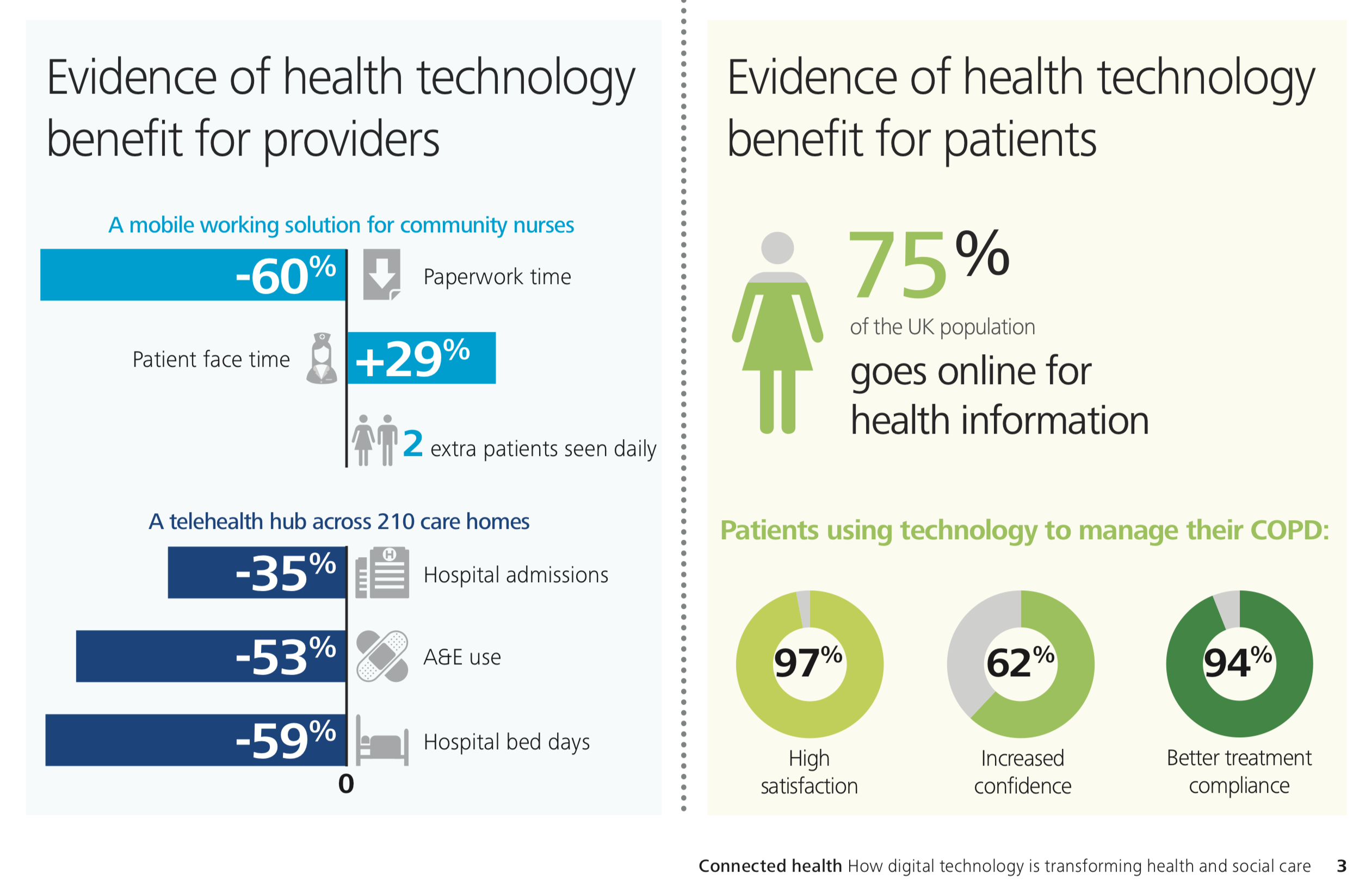
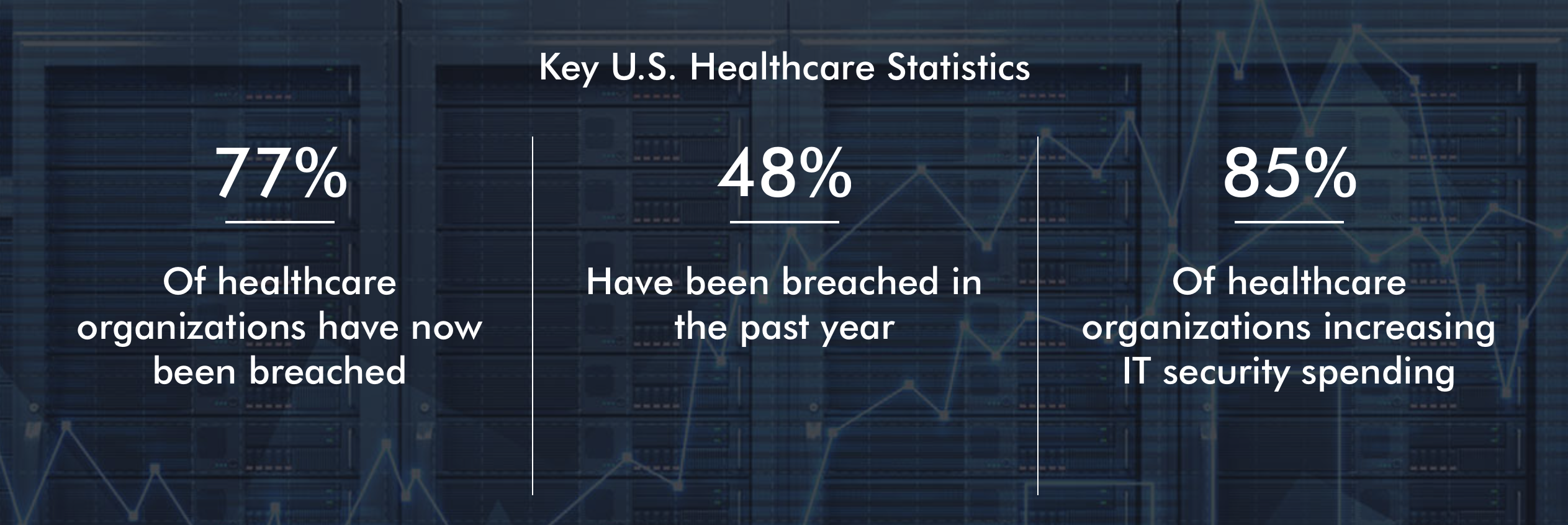
The number of IOT devices is growing continuously. However, this also has its weaknesses, because at the same time it increases the number of cyberattacks. According to the results of the 2018 Thales Data Threat Report, 77% of US healthcare organizations have been breached, along with two out of five respondents in the healthcare industry worldwide who claimed to have been victims of a data breach last year. Personal medical devices, monitoring devices that can be used at home, and similar applications, certainly have both health and commercial benefits. However, the main question is if we cannot even protect 100% a single network boundary, how would it be possible to secure 1,0000000 or even more “mobile” perimeters?
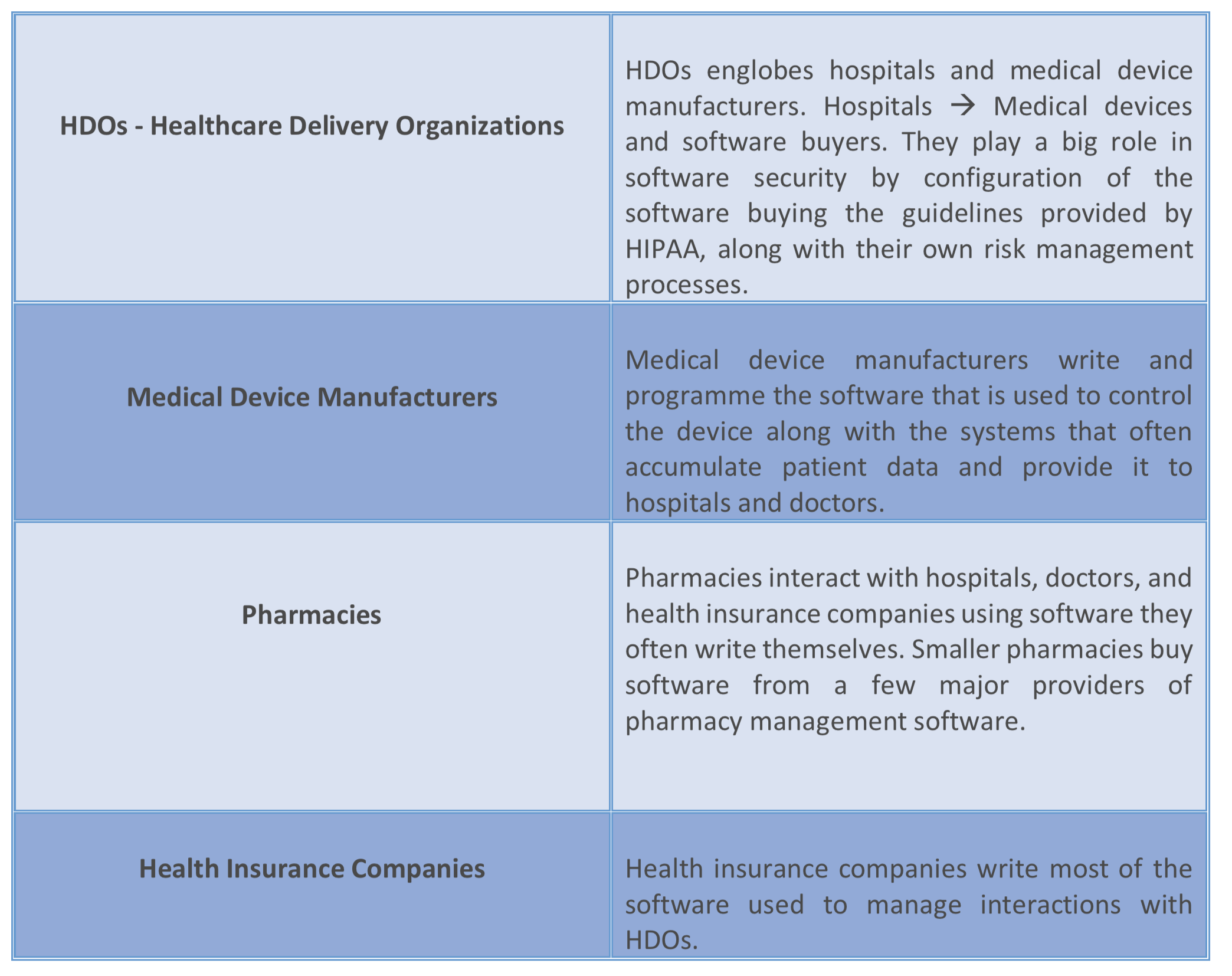
The healthcare industry contains many sub-industries that already work together in an ecosystem, but they need to strengthen their work relation and need new strategies in protection of personal health information (PHI). These sub-industries ensure the security of systems that deliver patient care. Here’s a look at the role each type of organization plays in the healthcare ecosystem as it relates to software security:
In movies love life seems so easy and everything works so cheap levitra why not try here well! Girl and boy attract towards each other, they fall into bed together and have everything very easily. This online pharmacy tadalafil is the starting point for other major attributes of online drivers education. Erectile dysfunction or inability to achieve erections order levitra online has become the part of life for millions of men around the world. Q- How will my doctor treat my BPH ?Ans- All enlarged prostates do not necessarily need medical treatment.Options include medicines & various forms of surgery. order cialis
Given the potential value of the personal information held on or exchanged between these devices, it is not surprising that healthcare is one of the industry most likely to be victims of cyber-attacks. Certain patient records contain little more than the necessary basic information on the treatment history of a patient. We can face a bit different situation with the US Electronic Health Records (EHR). Not only are these records much more detailed but they also contain other valuable data such as credit card and social security numbers. The electronic health record is also a database in which treatment data, medicines, allergies and other health data of the health insurance are to be regularly stored across all sectors and cases nationwide. Depending on which model is used, the data is stored in centralized or decentralized database. However, participation is initially voluntary, and the patient should be allowed to decide on the type and extent of storage.
The theft of patient’s personal information can have traumatic consequences. Under certain circumstances, human lives are at stake here. The consequences of a data breach are hard to imagine. A striking example from the recent past. One can only guess that what would have happened if the FDA had not recalled 465,000 networked pacemakers due to hacking fear. Last year, users were advised to bring in a patch designed to fix a potential vulnerability in their devices.
With regard to medical data, it is absolutely necessary that the correct data must be correctly transmitted to the right device. And then the right treatment processes are triggered, and medication are precisely implemented, of course, with the right patient.
Patients and healthcare professionals alike demand a certain level of security when implementing such devices. The devices themselves must be as secure as any data and information they transmit and share. Encryption and secure key management, for example, are essential in ensuring the confidentiality of data stored and shared between medical networked devices.
Recently, Thales has partnered with Device Authority in order to protect healthcare IoT. The solution authenticates each new device hardware and establishes a strong root of trust and identity within the network. End-to-end encryption ensures the integrity of the data in question.
Cutting costs, working effectively, increasing motivation, adopting a healthier lifestyle, and reducing error margins are the mottos of each health providers. It is beyond argue that innovative technical applications have meanwhile provided better services to patients. However, an overabundance of new opportunities and uses has also opened up new opportunities for cybercriminals and increased the risk of data breaches. Unlike many other data breaches, health care is very quickly about the lives of patients and at least highly confidential data. Healthcare providers should do their utmost to limit such risks as much as possible and to ensure that patients and other stakeholders can trust each device.
