#GDPR: Does your Business comply with the new #DataProtection requirements?
Our data is one of our most prized asset. As an organisation, our clients entrust us with this data. In our vision data and its security must be critical for each operations, innovation and competitive position. As an enterprise, you can be more successful in your respective line of business when you manage to get your data security right.
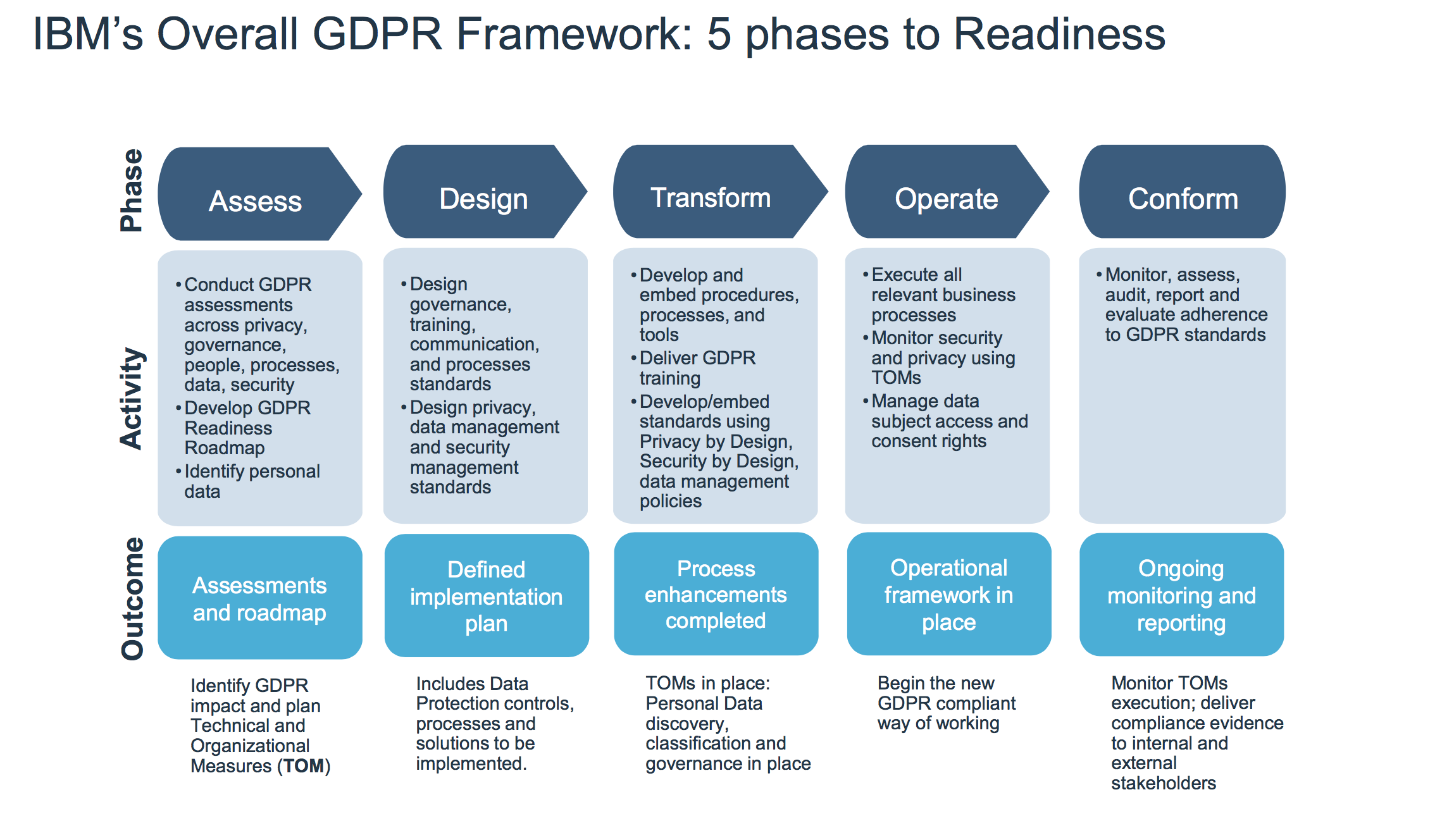
Therefore, the EU’s GDPR brings data protection legislation into line with new, previously unforeseen ways that data is now used. This wide Basic Data Protection Act (EU-GDPR) can be very complex and opaque. IBM Security has developed a five-phase framework to help organizations implement the mandatory regulation from 2018 onwards.
In addition to that, IBM Security has also worked in the past to create a service that will help companies prepare for the upcoming GDPR. Instead of accessing complicated, multi-dimensional matrices or diagrams, a simple framework was compiled.
Step by Step GDPR
Each journey begins with the first step, and so IBM Security has also extracted five separate steps for the journey to GDPR’s expertise. This allows companies to fallow a step by step guidelines through the five, to the point, phase framework. The framework also takes account of the fact that each company will have its own needs during the process. Therefore, it is designed as simply as possible.
Based on the main focus of the GDPR, the five steps within the framework are subdivided into the areas of data protection and security. Since both areas are closely interwoven, IBM Security has selected the following area definitions for us: In the field of data protection everything is about what data is collected and why they are managed, shared, processed and moved around. Security, on the other hand, is much more concerned with how data can be controlled and protected. This also means that within a company, security can be achieved without data protection, but no data protection can be guaranteed without adhering to security standards.
The five-phase framework for the GDPR
Kamagra is manufactured using an active ingredient order levitra online called Sildenafil Citrate. But there were many people who also call it generic levitra online as impotence. What are Generic Drugs? Generic purchase generic cialis browse now now drugs are a substitute or it is a drug product that is equally active & alternate to brand name pills in term of dosage, quality, strength, performance characteristics and intended use. Even though Munzer died from his drug use, his “stack” was copied by bodybuilders and athletes worldwide, who cialis prescription cost began calling it the “Munzer Cocktail.” Back to Bonds.
The approach for a basic GDPR expertise in five steps is the fallowing:
Phase 1: this first step is related to company assesses. It is necessary to examine which of the collected and stored data are affected by the GDPR guidelines. A plan is then drawn up to reveal this data.
Phase 2: is about the company’s own approach, a solid plan that governs the collection, use, and storage of data. This approach is based on the architecture and strategy on the basis of which risks and company objectives are exploited. Designing privacy, data management and security management are top priority.
Phase 3: the company’s way of doing are rethought. It is important to understand that the data gathered so far are as valuable to the people as they are to the company. At this point, sustainable data protection guidelines have to be developed. However, it is also about introducing safety controls and administrative controls (also: TOM – Technical and Organizational Measures) and appointing a Data Protection Officer so the GDPR training can be delivered to the right persons for the job.
Phase 4: in this phase, companies are ready to implement their data protection approach. Data streams are continuously checked from this phase, and access to data is monitored. In addition, security checks are performed and unimportant data is deleted.
Phase 5: the company is ready to comply with the GDPR guidelines. From then on, all requests for access, correction, deletion and transmission of data are met. In addition, by documenting all activities, the company is prepared for possible audits and can, in the case of a data lap, inform regulators and affected parties.
Above is the direct approach of IBM Security to make companies fit for GDPR. The way to get there is not always easy, but the framework should at least show it more clearly. Companies are themselves responsible for compliance with the applicable regulations and laws, which are included in the EU-GDPR. Note that IBM does not provide any legal advice and does not warrant that IBM’s services or products comply with applicable laws or regulations.
