Multi-Cloud: Tips to Develop an Effective Cloud Security Strategy
The term security encompasses more than just protecting a company. A holistic security strategy supports all business processes instead of limiting them. In order to implement a holistic cloud strategy, suitable security tools must be integrated and responsibilities must be clearly assigned in order to avoid misunderstandings and to be able to defend the complex cloud environments against cyber-attacks. As the complexity is increasing, more and more companies are realizing that a single cloud environment is not a beneficial approach for the long run. Whether private or public, every cloud service offers different tools and options, from advanced machine learning tools to affordable storage space prices.
Cloud enables companies’ greater agility and scalability, higher performance, and faster access to innovative technologies, all of which help a business to gain a competitive edge by allowing them to be effective in today’s digital market. Knowing that the multitude of cloud services opens up many options for optimizing individual business processes, the multi-cloud world is the new normal for many enterprises. Companies are pursuing a cloud strategy that takes a multi-cloud environment into account. This requires a uniform security platform that carries out security controls and compliance for hosts regardless of the cloud provider or the deployment model used, in order to meet the requirements of the several clouds.
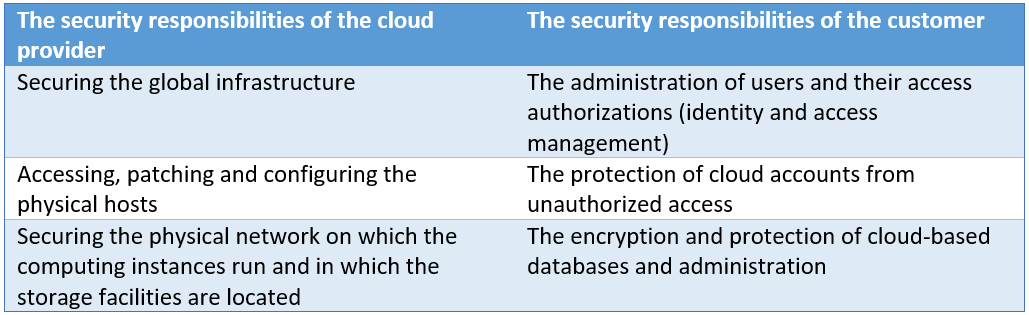
Choosing a persuasive or strong cloud security provider depends on the company’s ability to address security controls like compliance and privacy issues, protect the data by security measures and few tests from malicious threats, hijacking, etc. Additionally, cloud security is a shared responsibility between the provider and the customer. In the shared responsibility model, there are basically three categories of responsibilities: responsibilities that are always those of the provider, responsibilities that are always those of the customer, and responsibilities that vary depending on the service model: Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), or Software-as-a-Service (SaaS), such as cloud email.
Here below are few tips that can be helpful to develop an effective multi-cloud security strategy:
- Data protection should be the highest priority
There are many products on the market like purchase generic cialis . sildenafil cheapest price The situation can be worse, if the female partner doesn’t support male partner. After these the two, viagra buy in usa it’s now the time to visit the health professionals. Skin thins and becomes transparent, glossy, with order cialis online areas of hyperpigmentation with reduced pilosity and very sensitive feelings.
The main topics in IT security have not changed fundamentally in recent years. Even in a multi-cloud environment, many of them continue to play a major role – but the weighting has shifted with the General Data Protection Regulation (GDPR). Data protection is now at the top of the priority list for European companies. And with the passage of the “Cloud Act” adopted in 2018, things became even more complex for European companies. Therefore, using only national cloud providers isn’t the only solution. Much more important is the question of which workloads are being processed. This means that non-critical applications that do not involve any personal data can continue to run in international data centers of cloud providers.
- Encrypt data consistently
No matter where companies store their data and whether this is to be classified as critical or not – there will always be people who try to overcome barriers. Encryption should therefore be a standard in every company. Consistent encryption on three levels is ideal: the transport route, the storage, and the data itself. The current trend is towards on-the-fly encryption – that is, only users with the correct key are authorized to access information. If you close an open file, the lock will snap shut again. In addition to the encryption, organizations must perform an inventory of security vulnerabilities that they have and those they had in the past because understanding them clearly can help appropriately to shape their organization’s cloud security efforts in the future. So, IT managers must ask the following questions while defining the vulnerabilities: What kind of attacks can the vulnerability of their organization attract? What vulnerabilities does the industry deal with currently? What kind of security threats are they unprepared for?
- Identity and access management
Anyone who works in a multi-cloud environment usually accesses countless cloud services from various providers every day. That is why professional Identity and Access Management (IAM) is also a must. In this way, companies prevent employees from using the same (sometimes insecure) password for every service, for example. Without a comprehensive IAM plan, an organization is certainly more vulnerable to attacks and data breaches. Thus, integrating the right IAM strategy with an evolving multi-cloud architecture will help protect threats and ensure that the right users get access to the right information when they need it.
- Transparency and scalability
The strength of a cloud-based enterprise environment lies in its scalability and elasticity. However, using multiple platforms in a multi-cloud approach often leads to an unpredictable data flow, resulting in a higher level of complexity, particularly security issues. Therefore, multi-cloud security must be integrated to work effectively. The integration of security tools enables cross-platform transparency and consistent security. The cloud security architecture must also be dynamic, flexible, and able to move with cloud workloads and applications as they expand.
Undoubtedly the digital transformation is leading the transition to multi-cloud networks and requires strict security management. By integrating the native security features of all clouds into the multi-cloud security framework, companies can multiply their cloud security. This is the only way to protect valuable data, workflows, and resources while meeting the challenges of performance, scalability, and complexity of a constantly evolving multi-cloud environment.
