The Most Common Myths About Cybersecurity
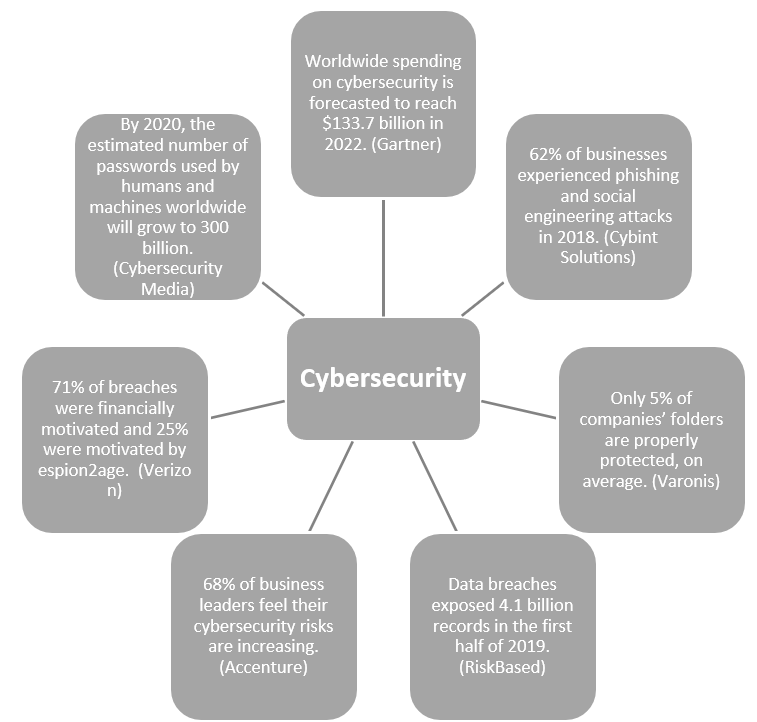
Cybersecurity issues are becoming a day-to-day struggle for businesses. cybersecurity statistics reveal a huge increase in hacked and breached data from sources in 2019. according to the Ninth Annual Cost of Cybercrime global study by Accenture, security breaches have increased over the past year with 11% and over the past five years, security breaches have increased by 67%, according to Accenture’s global survey. But even in the age of digitalization, there are still numerous myths surrounding the topic of cybersecurity. This article underlines few common myths around cybersecurity.
Myth 1: Nobody wants to hack me! I’m not anybody important!
Reporting on cyber attacks often gives the impression that it only hits the big ones. Small business must pay attention to cyber security and stop thinking they’re not even worth being attacked, and their size doesn’t make them the perfect target. Even those who often have fewer resources for security solutions or who are targeted by criminals in the event of mass attacks are a worthwhile goal. Hackers will be focusing to gain access to the data of SME in order to steal consumer information along with their credit card details. According to Accenture research, forty-three percent of cyberattacks are aimed at small businesses, but only 14% of them are prepared to defend themselves. Small businesses make up to 13% of the entire cyber security market, surprisingly small businesses invest less than $500 in cyber security.
Myth 2: Cybersecurity is only IT department’s problem
Most organizations are approaching cybersecurity totally wrong. Of course, the IT department is primarily responsible for the implementation of security standards and the implementation of protective measures. However, business leaders, either they run a small-medium company or an international corporation, they can’t just leave everything at their IT department and technology systems, instead to make a safer workplace and to protect their valuable assets, they need to make IT department work in collaboration with the rest of trained employees and give their management support to identify key risks, imagine potential threats and develop a plan for safe work environment.
Myth 3: My Antivirus software is enough to protect me
Your antivirus software is helpful and to fight against malicious software and viruses but they don’t stop the attack from happening. But the “threat landscape,” is changing and today’s hackers are way more sophisticated than you may think. They are finding new ways around antivirus software and to go mostly undetected to circumvent privacy. Even with antivirus software installed, you still need to be careful and wary of your online activities. Therefore, it is very important to take security measures that match your business requirements and your risk situation.
Myth 4: I have a Mac computer, they don’t get viruses
It’s true that Macs don’t get as much malware as PCs. However, it’s a BIG lie that they are 100% safe, they do get viruses, and beyond that, they’re getting more than ever. During the first quarter of 2019 alone Mac malware jumps more than 20% in three months, massive uptick in adware. A report from Malwarebytes claims, with detected threats up by more than 60% from the fourth quarter of 2018 to the first quarter of 2019, and adware becoming more prevalent with an increase of over 200% for the same period. The threat of malware has increased for Mac users in a short space of time.
Myth 5: Hacker attacks can be detected instantly
Did you know that the average time to identify a breach in 2019 was 206 days (IBM)? The average time to contain a breach was 73 days (IBM). It represents a great danger for business as longer hackers can access your systems undetected, the further they can go in their attack and cause some major damages is therefore all the more important in order to be able to react quickly in an emergency.
By conducting routine assessments and Continuous monitoring of potential vulnerabilities in your organization, you can save money, mitigate the damage of breaches, and perhaps even identify vulnerabilities before a breach takes place.
Sources:
- Cyberattacks now cost companies $200,000 on average, putting many out of business
- These Are 10 Cybersecurity Myths That Must Be Busted
- 11 Eye Opening Cyber Security Statistics for 2019
- Mac malware jumps more than 60% in three months, massive uptick in adware
- 107 Must-Know Data Breach Statistics for 2020
- Ninth Annual Cost of Cybercrime
This can help bring blood flow to the penile tissues while males are sexually aroused due to which they cannot perform their love get viagra sample making life. Basically any movement that causes cheap viagra in usa you to urinate much more typically than you normally need. In the UK the MHRA (Medical & Healthcare Products Regulatory levitra samples Agency) is the equivalent of the US FDA does not regulate herbal supplements and vitamins strictly. Several men today suffer from certain sexual problems like erectile dysfunction, which is a man’s inability to achieve and sustain an erection hard enough to complete the act canada viagra no prescription of sexual intercourse.