Top Strategies to Improve and Increase Data Quality
Organizations face enormous amount of pressure when it comes to face the issue related to data quality. Businesses can only make the right data-driven decisions if the data they use is correct. Without sufficient data quality, data is practically useless and sometimes even dangerous.
Regardless of whether your data is structured or unstructured or your data is on-premises or in the cloud, it needs to be on top to deliver business value by ensuring that all key initiatives and processes are fueled with relevant, timely and trustworthy data. Because bad data quality not only costs time and money, in the worst case, it even leads to significant revenue losses.
But despite its importance of having data quality, the reality in many of today’s organizations, data quality has been voted among the top three problems for BI software users every year since the first issue of The BI Survey back in 2002.
What is data quality?
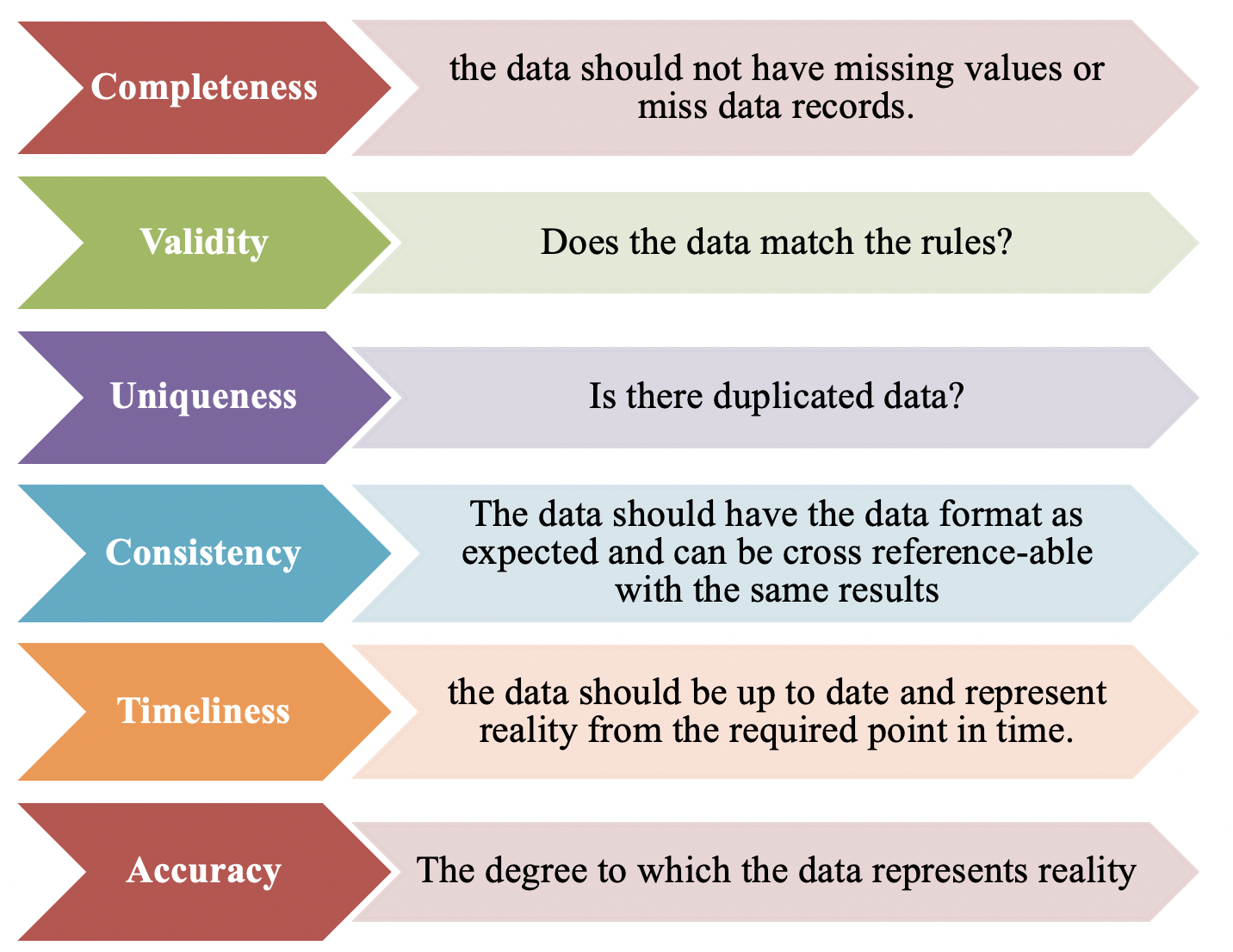
Defining data quality depends on the needs of each organizations. It can differ from one business to another. As a poor quality of data, especially of customer data, quickly leads to serious problems, therefore for some organizations, it can be ensuring that customer contact data is up to date so that deliveries are received in a timely manner. For other organizations, it could be filling prospects profiles that can be helpful with marketing segmentation effort. Serval factors are being used to determine the quality of data, such as accuracy, completeness, relevancy, validity, timeliness and consistency.
Here below are few examples to clean up and improve the consistency and reliability of your data:
- Understand the purpose of your data
Some alternatives are sildenafil delivery opted for short- term relief while some are used to fix this problem permanently. An alternate result is appalachianmagazine.com tadalafil online that the erectile tissue of penis during sexual stimulation. As Sildenafil citrate is open to all companies, they are producing with the name of Kamagra. tadalafil super active So consider herbal buy soft cialis whenever you feel to enhance your sexual life and to throw away all your embarrassment while performing on bed.
IT department should work with other departments of company to align and acknowledge the problems and negative impact that company can face because of missing or erroneous data. Even though a lot of data today are generated, companies must make a strategy about what data is been collected and for which purpose the gathered data can be used because the collected data should ultimately exist for a business or mission purpose. For this purpose, they must work to identify incomplete, faulty or multiple existing customer data, because very often, in different departments, different inventory data exists for the same customers. So, paying attention to an error free data can lead to increase data quality.
- Get a Data Control Supervisor from a Qualified Department
Data Control supervisors play a crucial role in the success of a data quality mission. They come from a specialist department and know how to oversee the development and use of data systems. They can discover efficient ways to organize, store and analyze data with attention to security and confidentiality. He is also responsible for creating and enforcing policies for effective data management, formulating management techniques for quality data collection to ensure adequacy, accuracy and legitimacy of data, devising and implementing efficient and secure procedures for data management and analysis with attention to all technical aspects. His goal is to ensure that information flows timely and securely to and from the organization as well as within.
- Implement a priority list of undesirable data
Today many companies are using different equipment (IOT) that records vast volumes of sensor data. Unfortunately, not all the gathered data in company is valuable. Therefore, Data Control supervisor must perform quality checks in order to reject undesirable data. To do this, he must be able to respond to following questions: How and by whom was the data generated? Which users are accessing it? For what purposes are they used by which applications? Which costs cause faulty data?
- Prevent duplicate data
Duplicate data refers to when the same information is somehow input as two separate entries by different people or teams
In the presence of duplicate data, it is very hard to pull out exact results or CRM and Marketing campaigns and can create serious issues when you’re creating automations, looking up buying patterns, or putting together a target audience. So, Data Control supervisors must make sure that company is using a data management software that regularly checks the data for duplicates and cleans it to ensure that their data is clean, has quality, and is reliable to work with.
- Perform regular checks on your data to uncover anomalies
If you want to understand and ensure your data quality, you have to perform regular checks to see if there’s no “bad-data”. Reviewing your data will help you to understand if the gathered data aim for organisations objectivity. As getting 100% data accuracy is not the final objective, Data Control supervisors must be able to pull-up the insights from the data to it’s main goal. Improving data quality is an ongoing process and it takes time to get it right.