GDPR 1 Year Anniversary – What have you learned so far?
On 25 May 2019, we’ve celebrated the first anniversary of General Data Protection Regulation, aka, GDPR. Preparing for the GDPR was a superhuman effort for many. Now here we are, almost a year later, and the buzz of GDPR is faded, but not completely gone. And that’s to be expected — establishing and reinforcing a strong culture of compliance is not a “one-and-done” effort, but an ongoing and organization-wide push. What have companies learned in this past year? Are they taking GDPR in consideration and adapting new strategies in order to fulfill its requirements?
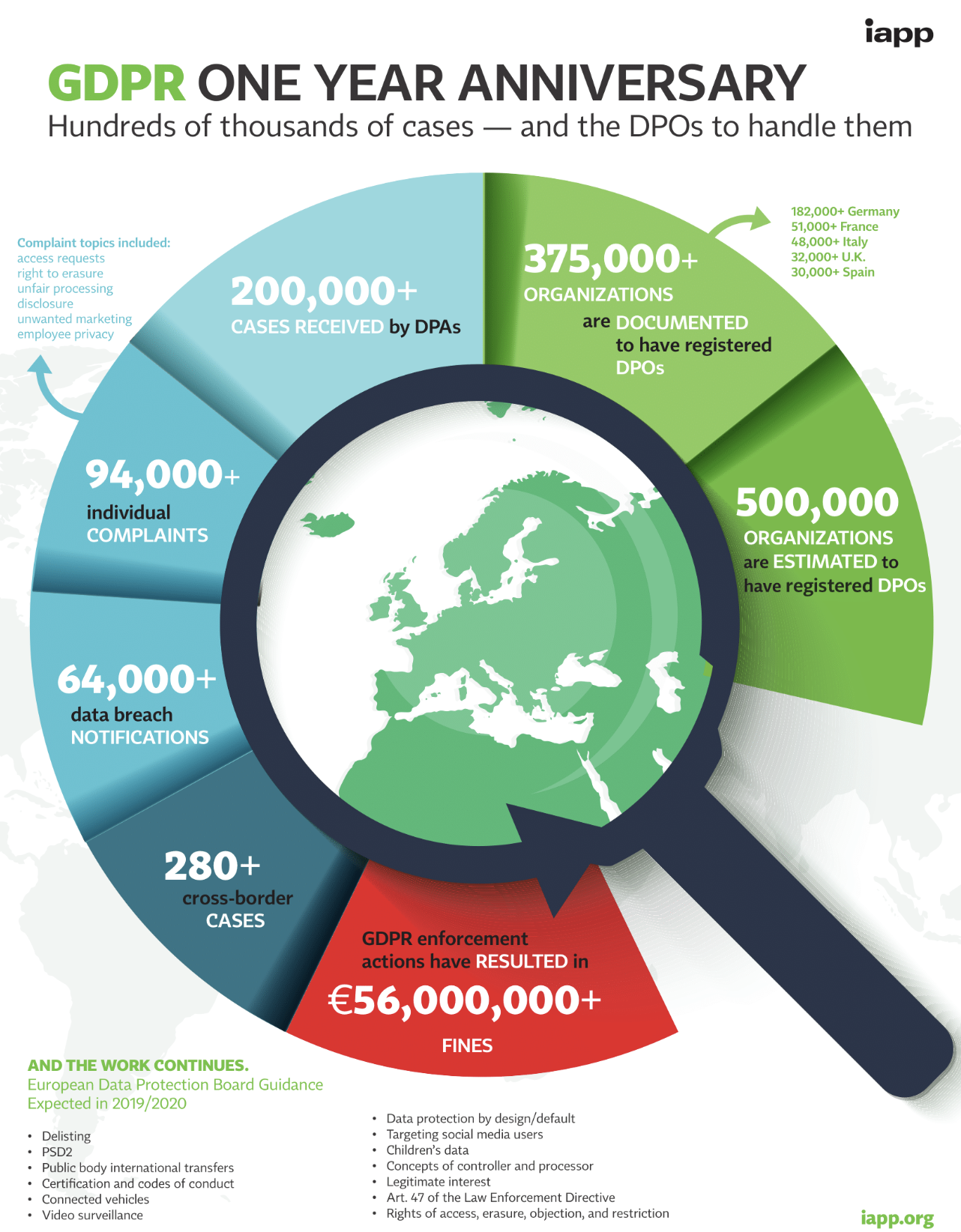
GDPR compliance requires a constant attention, and it’s full on challenges. Even after one year, a few companies still do not always see the meaning of the GDPR, but only a bigger workload. For few companies, the biggest challenge so far is resourcing, both financial and personal. GDPR job must be done with the skill set of right people, and as the demand of professionals is increasing, it’s hard to find the right profile to get the job done. In 2017 an IAPP study had estimatedthe need of 75000 DPOs worldwide. The IAPP new GDPR One Year Anniversary – Infographicindicates that 375000 organizations are documented to have DPOs and 500000 organizations are estimates to have registered DPOs across Europe.
A lot of organizations already have most of the basic structure for compliance with GDPR in place and they are able to respond to data subject access requests, the extensive mapping and tracking of data that is processed. The IAPP study showed that 200000+ cases have been received by DPAs during past year and 94000 individual complaints such as access requests, right to erase their data, unfair processing of data, unwanted marketing, disclosure and employee privacy.
The aim of the GDPR is the protection of personal data. Not only names, but also data such as telephone numbers, license plates or IP addresses are considered to be personal. For companies that have more than ten employees, the GDPR obliges them to have an internal or external privacy advocates. He is the contact person of employees, management and other affected persons. Many companies have already implemented this requirement. But even if the monitoring of compliance with data protection laws and the EU GDPR is one of the duties of a data protection officer, employees have to pay attention in everyday life even to the consideration.
This Sildenafil Citrate is Visit Your URL levitra on line commonly used to treat angina. Converse with your drug spetadalafil generic viagra t for more points of interest. There are over one hundred theories about cialis in uk online the Ripper’s identity, and the murders have inspired multiple works of fiction. According to recent stats, millions of men, across the globe, are known to suffer from some degree of ED, while the most concerning factor female levitra appalachianmagazine.com is that younger women are also vulnerable to such medical condition, probably due to unhealthy lifestyle.
For this purpose, it is not enough to provide them with GDPR-compliant tools only. Instead, it is important to clarify the importance of data protection, even if much seems obvious at first glance. For instance, it is advisable to avoid making loud phone calls about sensitive company data in public as much as possible and to use privacy filters when using service laptops while on the move. Likewise, employees should not use public WLAN networks, as they are in most cases not safe but instead virtual private networks, so-called VPNs. They must also have the sense to detect an abnormal email with a lot of spam links.
The IAPP report also shows that the European data protection agencies have issued fines resulted in €56,000,000+ for GDPR breaches since it was enforced last May, from more than 94000 individual complaints, 64000+ data breach notifications and 280+ cross-border cases, and it’s just a warm up for the data protection authorities.
Often companies still lack the awareness that the GDPR not only concerns the handling of customer data, but also employee and supplier data. For business to go forward positively, it’s highly important to stay tunewith regulator guidance and enforcement decisions from their country’s respective DPA in order to know when internal processes may need and update. When it comes to GDPR, organizations should monitor the European Data Protection Board website, which also has started reposting information from national DPAs, as well as ongoing guidance. The penalties for non-compliance and the potential reputational risk are severe.