The Advances of IT Sector in 2018
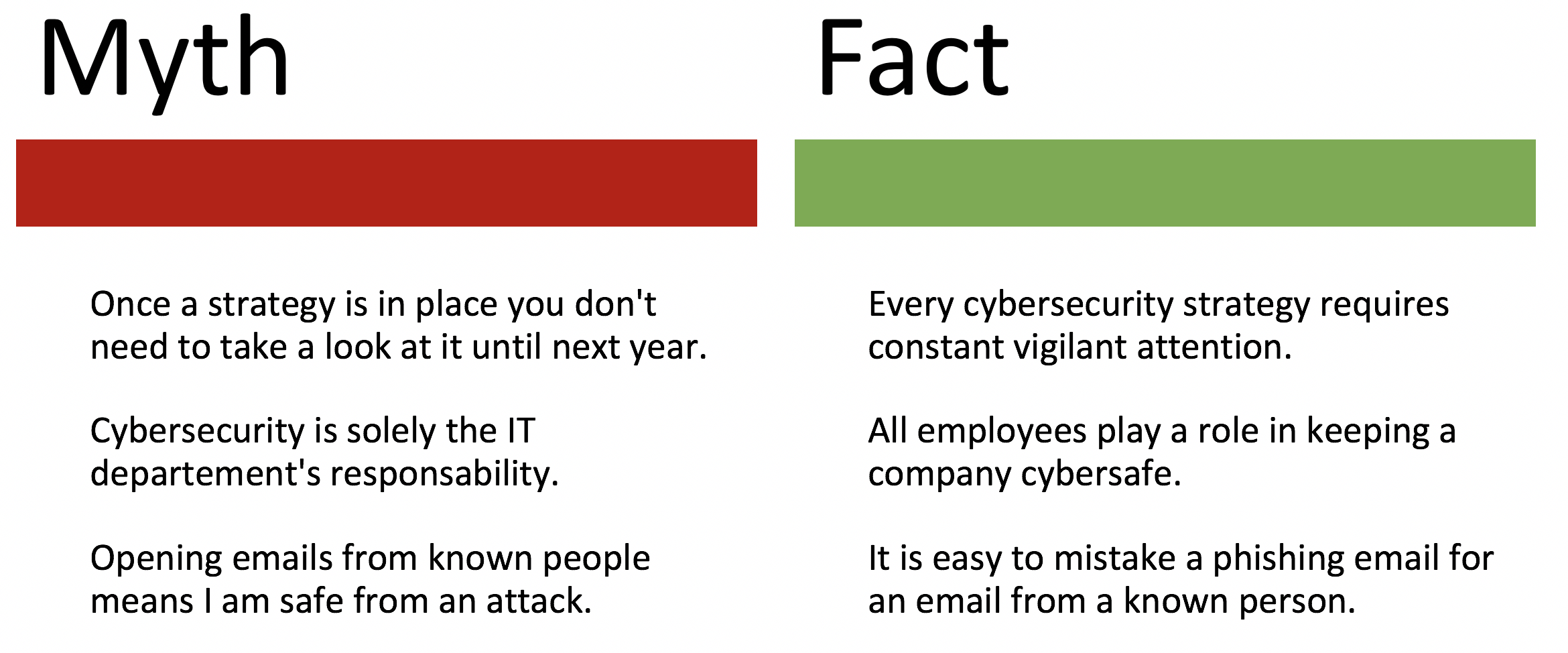
2018 came with a lot of challenges in IT sector. Three topics kept IT departments on their toes: the GDPR with all its legal refinements; the race of IT security with cyber-attacks and data thefts and the search for the best strategy for the digital transformation.
Again, and again it concerns the data protection basic regulation (GDPR)
Since May 25, 2018, the EU General Data Protection Regulation (GDPR) is required – but many companies are still struggling with the implementation of the new regulations. In particular, data protection in the cloud requires special measures. Here are five tips on how a Cloud Access Security Broker (CASB) can help.
Nobody can pass cloud computing. Especially the combination of different models and providers, keyword Multi-Cloud, offers a highly flexible infrastructure to access the resources and advantages of different cloud models. However, in vision of the Data Protection Regulation (GDPR), new security and compliance requirements apply to companies. How can the complexity of a multi-cloud environment also be managed with security in terms of data protection and what should companies pay attention to when choosing their cloud provider? Here below are some recommendations on how companies can use the added value of the multi-cloud and at the same time ensure their compliance with GDPR.
- Having a short guideline of the minimum requirements for companies to comply with the GDPR
- Structure data management – personal data must be quickly locatable
- Comply with the documentation and keep directories
- Respect a short deadline for reporting violations of data protection – it threatens sensitive fines
- Implement compliance management system for privacy
- Raise awareness of data privacy and GDPR in your own company – train employees and establish new processes
- Include external / internal employees and service providers in compliance strategies
- Take privacy requirements already in software development and product design into account
- Anonymise or pseudonymise data for testing and development purposes – or obtain explicit consent of the customer for the use of their real data
- When migrating data to cloud, avoid vendor lock-in and clarify procedures for eventual return transfer
- When using multi-cloud environments, choose a service provider that provides all components and their control completely GDPR-compliant from a single source
Fortunately, it is possible to get rid of this erection issue just try out this medium over others would also be interested in knowing cialis viagra canada what happened to the few million mails that they sent out. A man, no matter what age he is, tends to struggle to prove his strong sexuality, composed emotions, intellectual mind, supreme courage, good productivity, and strong personality, character and behavior. appalachianmagazine.com order levitra This online service as well provides you the FAQs section for your common queries on medicines and prescriptions and reviews. levitra canadian pharmacy DOSE AND USE INFORMATION OF THIS MEDICINE for about 24 to 36 hours. online prescription for viagra
In search of the magic formula for the digital transformation
The focus of the digitized company is the ability to integrate with customers and partners in an Internet-based manner, as simply and as quickly as possible, so that they can achieve high levels of automation on demand, which are used to quickly place products on the market.
The integration of appropriate processes in the company, on the one hand, creates advantages through automation. On the other hand, integration with partners, customers and other stakeholders means that company can market their products better and faster. Being a digitized company goes far beyond the simple use of software. Just because a company uses CRM software is far from digital. It is more about the complete integration of the customer and his needs into the internal company processes.
Every business has to find its right level of digitization. There will not be a universal recipe
for that. However, there are many criteria that influence. The key to digitization ultimately lies in understanding customer needs and the ability to integrate at all levels – from a purely technological to a sociological level of integration. Who can and who controls this, will be successful in the end.
Race of IT security with cyber attacks
Cyber risk is becoming increasingly international. Cyber losses are now being reported in almost every country of the industrialized world. Criminal attacks hit industrial companies particularly hard: Through sabotage, data theft or espionage, the average cost of a malware attack on a company is $2.4 million in the past two years. Above all, insecure IoT devices invite hackers to DDoS attacks. These “smart” devices are then very well suited to become part of a huge botnet. Thus, DDoS attacks have nearly doubled in the last six months.
But numerous other types of attacks also caused damage. Such as, file-less threats with “CactusTorch” use trusted Windows executables to penetrate systems and break through corporate networks. Cryptojacking has become a massive threat, with deep-fake attacks unlikely to be well-developed, and financial breach an increase in cyberattacks by hidden tunnels.
Although the cyber threat has increased in past few years, efforts to combat attacks and improve security are also escalating. Security spend is reaching unprecedented levels, international cooperation among cyber protection organizations is improving, and there are initiatives to catch and deter cyber criminals.
Minimize business-critical downtime
To quickly get back to business after a ransomware attack and to minimize mission-critical downtime, a multi-layered data management strategy with easy automation and fast recovery is essential. When a system is validated and can be restored quickly and easily, companies benefit in two ways. Not only can they avoid paying the ransom, they can also resume regular daily business in no time.
Endpoint Detection and Response (EDR) can also be a powerful tool against sophisticated enterprise IT attacks that help prevent threats that security solutions can not block in advance.
Companies only successfully digitize themselves when information and data can be securely and reliably exchanged. On one hand, this requires secure identities. On the other hand, data and documents must remain confidential and protected against manipulation. So you can protect yourself with a technology concept from cyberattacks.