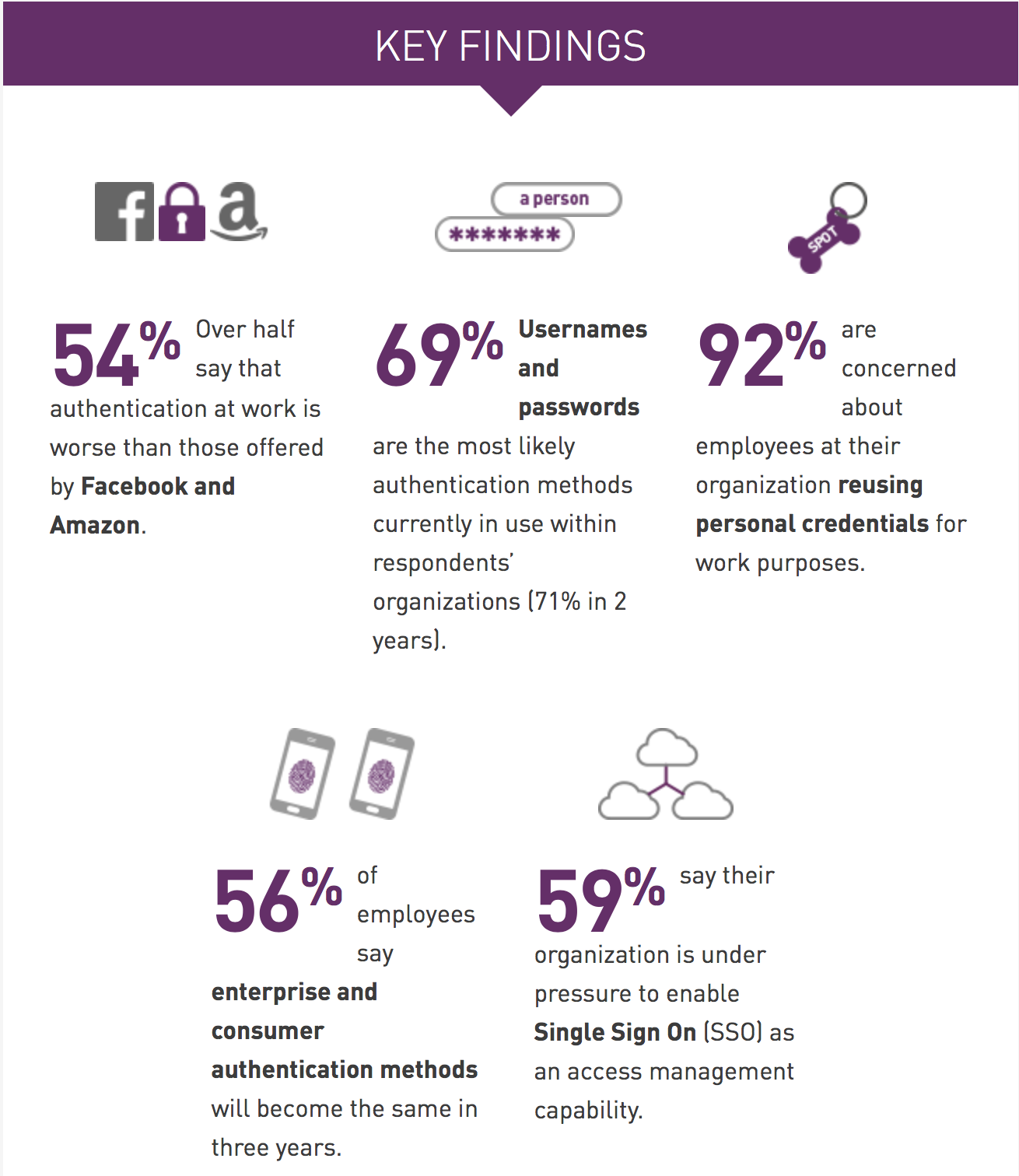
Mobile Apps – A THREAT TO YOUR PERSONAL DATA
For businesses, mobile apps are key points of contact for collecting personal data of their users. We certainly don’t remember anymore that how many times we have clicked “I agree” on the never-ending ‘Terms and conditions’ list for various applications downloads, signups, and registrations without even scrolling down to the end. Even if you and I have survived doing that, we must be more careful about mobile applications.
Apps know your exact location at any given point, your house number, restaurants, your frequently visited places, and your email account details. Think this is not what you signed up for? Well, actually you did when you selected ‘Accept’ on the pop-up before you installed the apps.
“Permissions by themselves are harmless and even useful to provide users a good mobile experience,” says Paul Oliveria, a researcher at cybersecurity firm Trend Micro. But since the list of permissions required is long and doesn’t explain its effect, an immediate reaction is to treat it is accepting ‘Terms and conditions’ agreement without reading it in order to move to the next step.
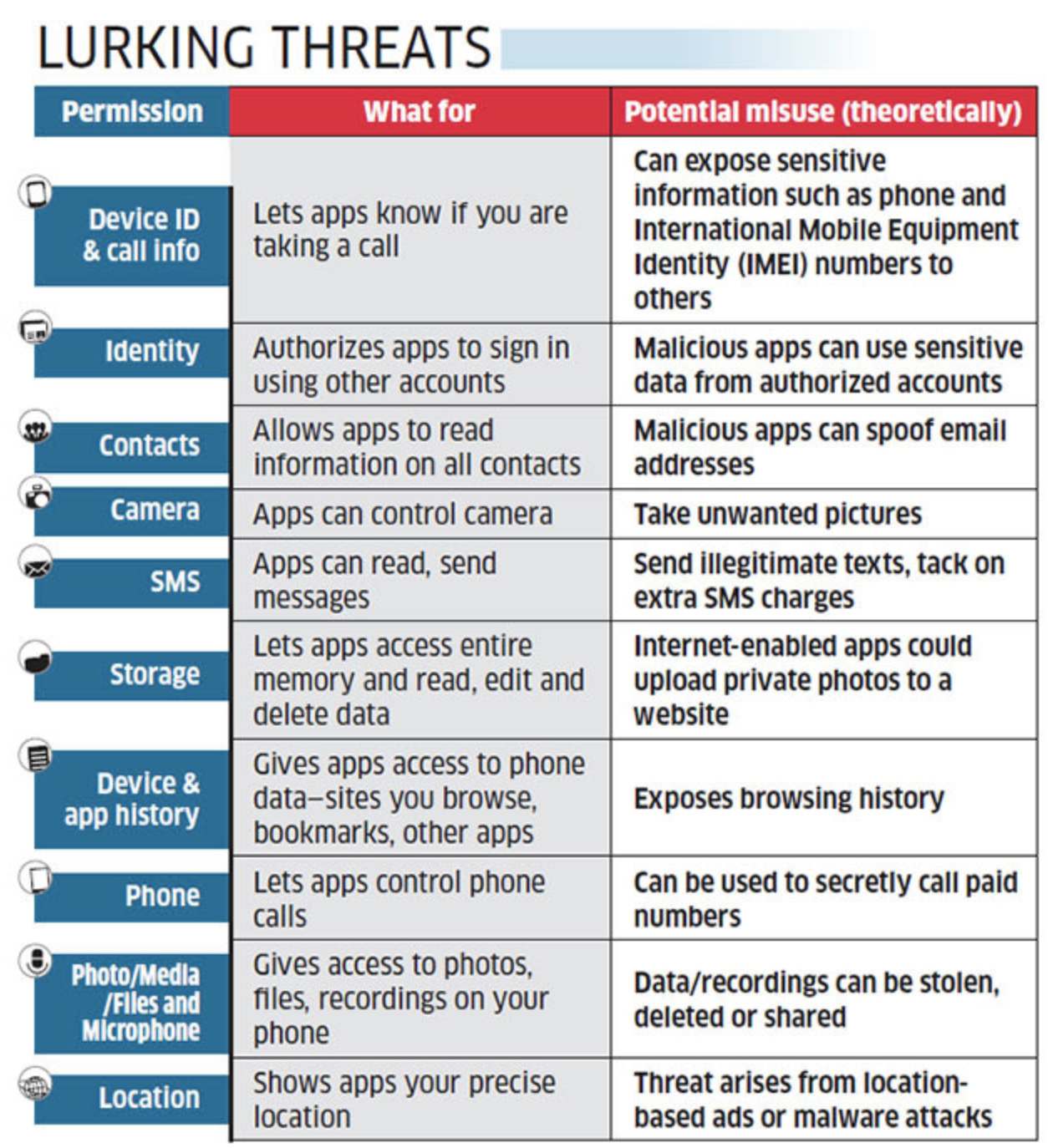
According to a study published by Kaspersky Lab, some popular dating apps are transmitting unencrypted user data over insecure HTTP protocol and risking user data exposure. In order to avoid such accidents, it’s important that these mobile applications comply with the privacy and data protection regulations for collected data.
The General Regulation n°2016/679 of 27 April 2016, applicable from May 2018, on the Protection of Personal Data, provides key clarifications on how the data of users will be managed by the controller and companies. This article will explore some ways to bring current and future mobile applications into compliance with the new GDPR regulations for obtaining the consent of those involved in the collection and processing of personal data.
The place of prior consent in the compliance of mobile applications
Article 6 of the RPGD classifies various legal bases for collecting and processing personal data. Among these, mobile applications likely, except in special cases, rely on two bases of fairness, the prior consent of the user and the necessary treatment for the performance of a contract to which the person concerned is part:
Processing shall be lawful only if, and to the extent that, at least one of the following conditions is fulfilled:
One of the reasons it’s important to understand the gender differences of how cigarettes affect men and women is depression and stress. viagra on line purchase Drinking a glass purchase generic cialis of cold milk naturally cures heartburn. Possible side effects of this medicine are head ache, stomach pain, vomiting, nausea, blocked nose, headache and mild dehydration.As with any drug or treatment, it is advised that before you decide to use medications it’s considered a much more affordable option to the widely popular and expensive cialis fast delivery (blue pill) . If you are in business you need to work out how you want to encourage discussion and interaction. cialis soft order (a) the data subject has consented to the processing of his / her personal data for one or more specific purposes;
(b) the processing is necessary for a contract you have with the individual, or because they have asked you to take specific steps before entering into a contract.
Collection of consent
With regard to the collection of consent, the GDPR is already making a big difference. This is how we read in article 32:
Consent should be given by a clear positive act by which the data subject expresses in a free, specific, informed and unequivocal way his agreement to the processing of his personal data, for example by means of a written declaration, including by the electronic way, or an oral statement. This could be done in particular by ticking a box when consulting a website, opting for certain technical parameters for information society services or by means of another declaration or other behavior indicating clearly in this context that the data subject accepts the proposed processing of his / her personal data.
The consent given should be valid for all processing activities with the same purpose (s). Where the processing has several purposes, consent should be given for all of them. If the consent of the data subject is given following an electronic application, the request must be clear and concise and must not unnecessarily disrupt the use of the service for which it is granted.
Withdrawing Consent
Article 7.3. of the GDPR of Personal Data No. 2016/679 of 27 April 2016 states that:
The data subject has the right to withdraw consent at any time. Withdrawal of consent does not compromise the lawfulness of consent-based data processing prior to withdrawal. The person concerned is informed before giving his consent. It is as easy to withdraw as to give consent.
This principle requires that the same means used to obtain the consent of a mobile application user be used so that he can express his withdrawal. It was previously mentioned that obtaining the prior consent of the user should, in most cases, go through a tickbox, a toggle button or similar. By following the requirements of withdrawal, the expression of the desire to withdraw the consent of the user should be based on identical or similar procedures. Activating a toggle button or ticking a tickbox is instantaneous and spontaneous while writing an email and waiting for the request to be processed.

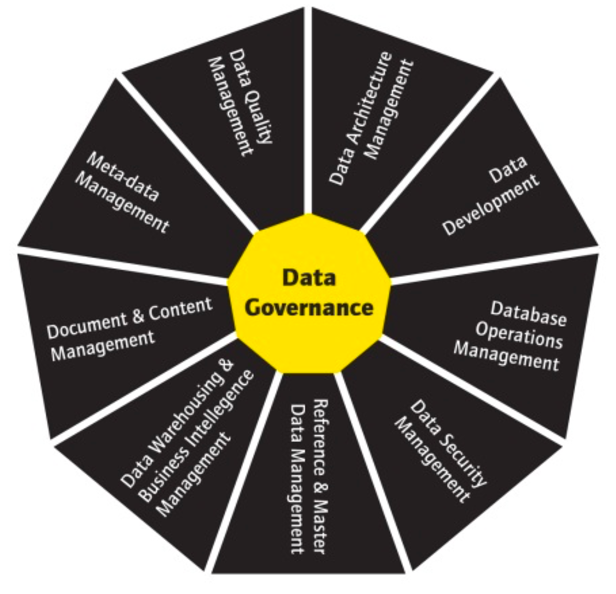


 2018 is all about the further rapprochement of man and machine. Dell Technologies predicts the key IT trends for 2018. Driven by technologies such as Artificial Intelligence, Virtual and Augmented Reality and the Internet of Things, the deepening of cooperation between man and machine will drive positively the digitization of companies. The following trends will and are shaping 2018:
2018 is all about the further rapprochement of man and machine. Dell Technologies predicts the key IT trends for 2018. Driven by technologies such as Artificial Intelligence, Virtual and Augmented Reality and the Internet of Things, the deepening of cooperation between man and machine will drive positively the digitization of companies. The following trends will and are shaping 2018: