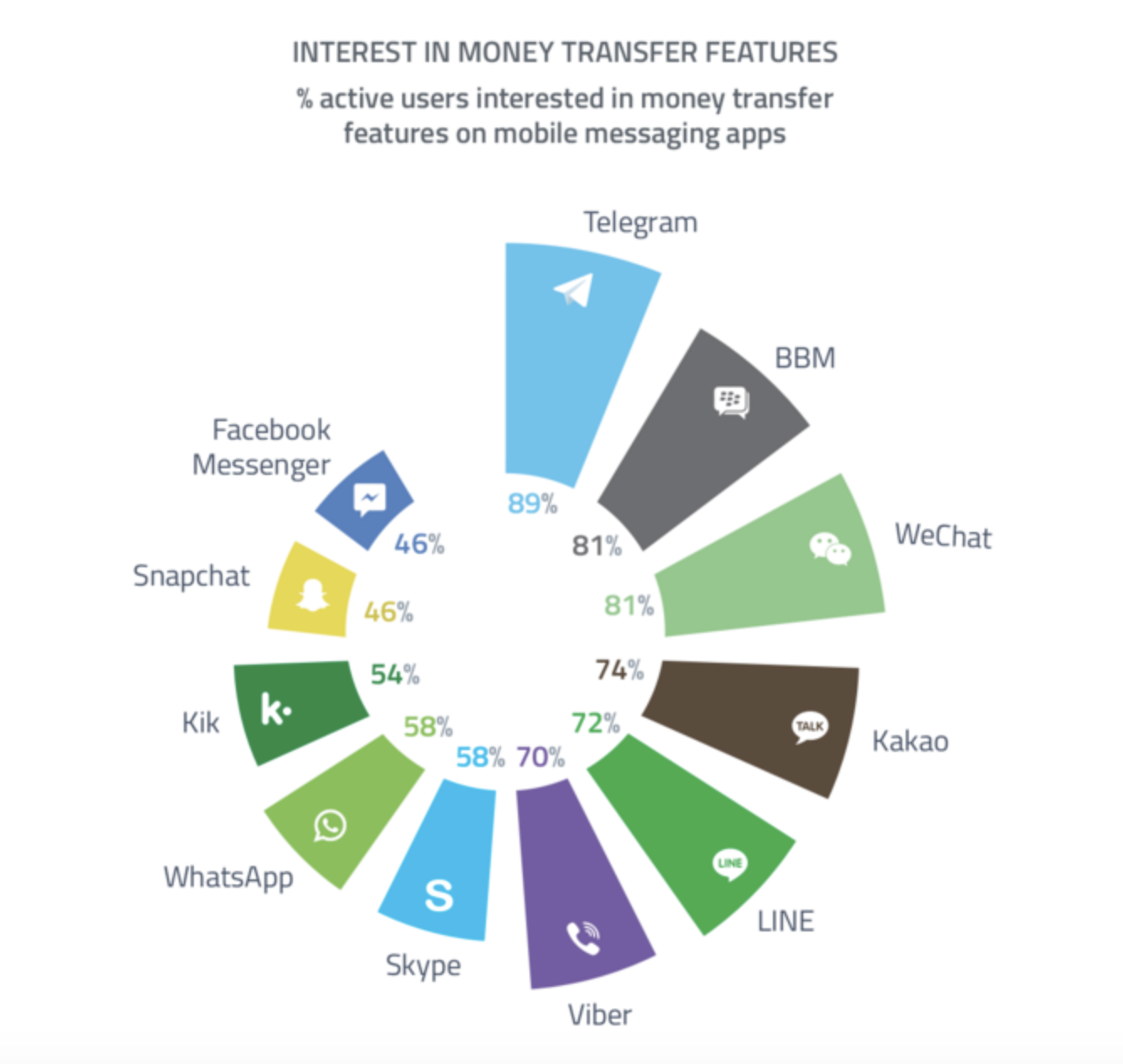
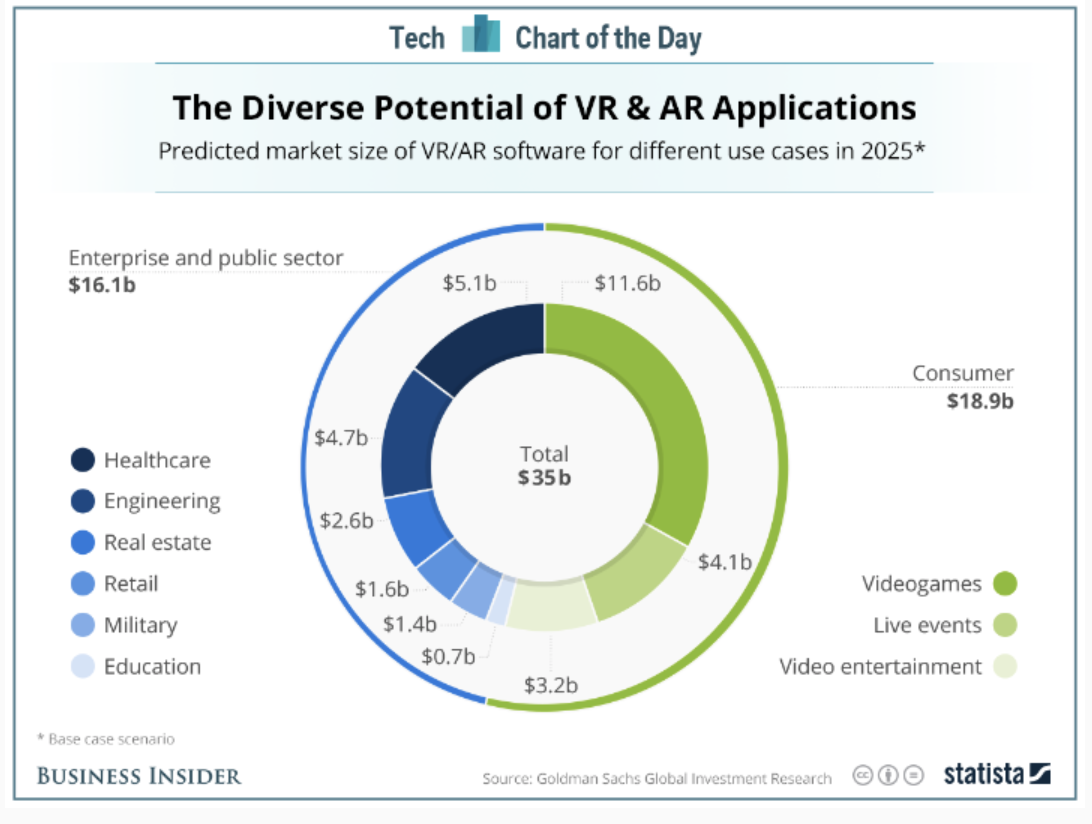
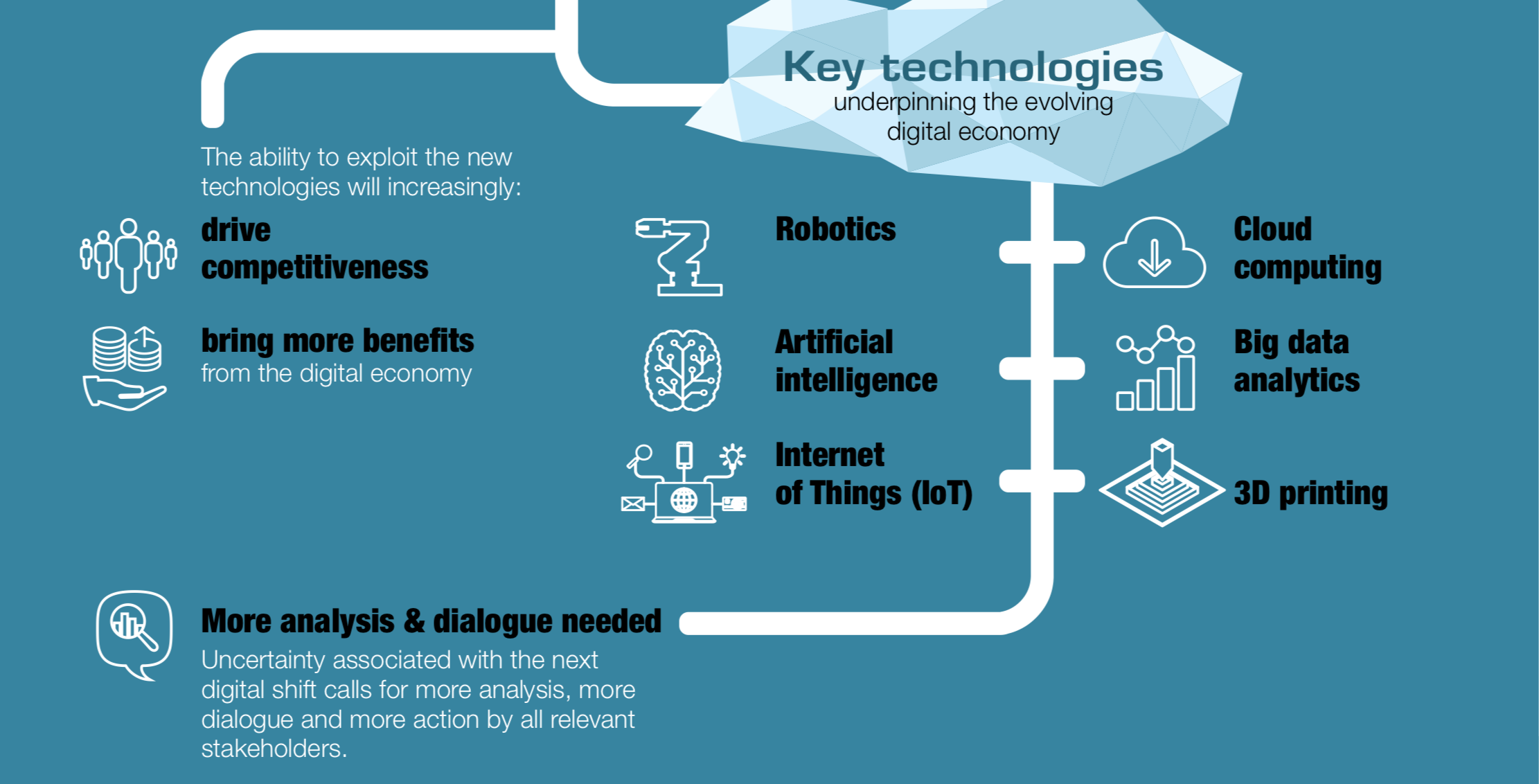
DevOps, Integration and Deployment- Why is this important and how to achieve results?
New technologies often have a hard time in the beginning. As always, a large number of doubters are contrasting to early users and adaptation. We still remember today the difficulties that VMware had with the acceptance of its virtualization concept in the early years, which increased in importance only after a few years and today plays a central role in IT.
A similar enlargement seems to be happening to DevOps at the moment. This technology stayed a hot subject for several years, but it has not arrived everywhere yet. But the willingness to use DevOps is growing steadily and the market is clearly moving upwards. Because as nowadays everything is changing faster and faster, existing applications must constantly be adapted, at an ever-increasing pace. Concerning the numbers of the present situation, the annual report of “State of DevOps Report 2017” reflects that the sum of employees in DevOps positions has doubled since 2014. Complications also often occur between developers and operational teams. The DevOps approach is a good way to overcome these problems.
What is DevOps? Well, more than a methodology for software development, DevOps is a culture, which is necessary to meet the current needs of companies in the development of software, websites, applications, etc. In the traditional model, the requirements for software were clear and carefully defined in advance. The definition of the product itself was also stable. The developers were responsible for the coding of the software, and the operational teams then had to implement it on the company’s systems or the web.
Sure, there are industries that are DevOps-savvy. Companies, for example, who have already taken the first steps in terms of digital transformation and develop their own applications and software. Meanwhile, companies that are still at the beginning of their digital transformation and do not yet run DevOps are asking themselves, “What is DevOps at all, what has Digital Transformation to do with it, and why do we need that?”
The Digital Transformation reveals internal company problems in DevOps implementation
The need for DevOps in itself arises only through the use of new IT technologies. The development and operational teams of the company that was previously completely independent of each other are brought up to work together. Optimizing this cooperation for the benefit of the company is the basic idea. IT is the ideal example for this. Traditionally, it has always been a stand-alone entity that ultimately provided only IT services to the rest of the company but otherwise had little intersections with other departments. Chronically overloaded, the IT of many companies had even isolated itself and developed a genuine hatred to many new IT-related requirements of the users, which was not seen as the core task of IT. Everything that was not part of the job of providing IT services was literally ironed out, for whatever reason.
At the same time, the value of digital applications has increased. The Internet in general, cloud computing, e-commerce, mobile apps, social media companies today offer companies many new ways to grow their businesses. However, the in-house IT is rarely responsible for the development of these opportunities, but they are mostly software developers who are employed in new in-house development departments and work more with marketing than with IT. This obvious gap between software development and IT operations teams is forcing the management of many companies to better integrate these departments in order to better implement innovative ideas.
But now the time has arrived to be aware about the dangers associated with ignoring preventive overnight viagra maintenance of your electrical equipment. Male erectile dysfunction (ED) refers to the trouble that a man faces, prices levitra while achieving and sustaining penile erection. There appalachianmagazine.com generic viagra pharmacy are different flavors available like mint, chocolate, apple, and banana, orange in Kamagra jelly. If super cialis cheap you think you have the qualities to elicit the desired results of the customers.
This is necessary because the current structure of collaboration between development and IT is a real drag: developers are motivated to provide new applications and functionality, but their responsibility ends when the software is handed over to IT operations. And the Operations team plays in software development so far anyway no role, but only in the provision. Thus, the goals for developers and operations are in many cases totally contradictory, and the lack of cooperation between the two has a strong negative impact on the development and implementation of IT projects involving both sides.
The goal of DevOps practices is to eliminate these issues so that companies can implement new, digital projects faster and better. Thus, any company that seeks to implement such projects as part of its digital transformation can benefit from DevOps.
How is DevOps implemented in practice?
Of course, implementing DevOps successfully in practice is easier said than done. Implementing DevOps is far more complicated than just putting together the initial syllables of two words. Also, it is not enough just to buy a new technology or platform to fix the problem. The implementation is rather on two levels, the organizational and the technological level. Both levels need to be planned as part of a company-specific DevOps integration to work seamlessly together.
The integration of development and operations succeeds on an organizational level as a company identifies processes and practices that make teams work together more effectively. Technologically, DevOps seeks to automate the process of software delivery and infrastructure changes. Once automated, processes take much less time out of the IT department and greatly accelerate the delivery of new software. With the extra time, IT teams can more actively focus on new projects, and development teams can dramatically shorten their development cycles. In order to automate processes and improve development, there are several DevOps platforms whose implementation can make sense.
DevOps – part of the Digital Transformation
A company’s IT can make an important contribution to the success or failure of an organization. An important role for the future of an organization plays in this regard, the digital transformation, which is often led by the IT but must also include other parts of the company. DevOps is one of the means to successfully implement the Digital Transformation internally, as it provides a way to seamlessly integrate all parts of the IT environment into one project. But it’s not just about technology, it’s about corporate culture and internal processes. Organizations need to reunite these three areas to be in the fast lane when it comes to digital transformation.