Internet of Objects Will Reach €250 Billion in 2020
BCG expects that by 2020, € 250 billion will be devoted to IoT technologies, products and services. Among the studies examining the adoption of new technologies and investments in the IoT sector, the recent market analysis of the Boston Consulting Group offers a whole new vision.
The total number of IOT connections is expected to grow from 6 billion in 2015 to 27 billion in 2025, an annual growth rate of 16%, according to Machina Research’s annual report.
The B2B market for the Internet of Things (IoT) is increasing day by day. Software-Hardware vendors, Service providers are all in competition to get the biggest market share. And to get the biggest piece of cake, every IOT provider’s concern is to know where are the growth opportunities?
Annual growth of at least 20% in the overall market
The two main sources of growth in the IoT market will be investment in services and applications. Here are the main points raised in the new BCG market study. Between 2015 and 2020, BCG expects revenues from all IoT sectors to grow at an annual rate of at least 20%. B2B customers are more focused on services, IoT analysis and applications, making them the fastest in terms of growth. By 2020, these layers will have captured more than 60% of the IoT growth. Moreover, each of these layers is expected to generate 60 billion euros of expenditure by 2020.
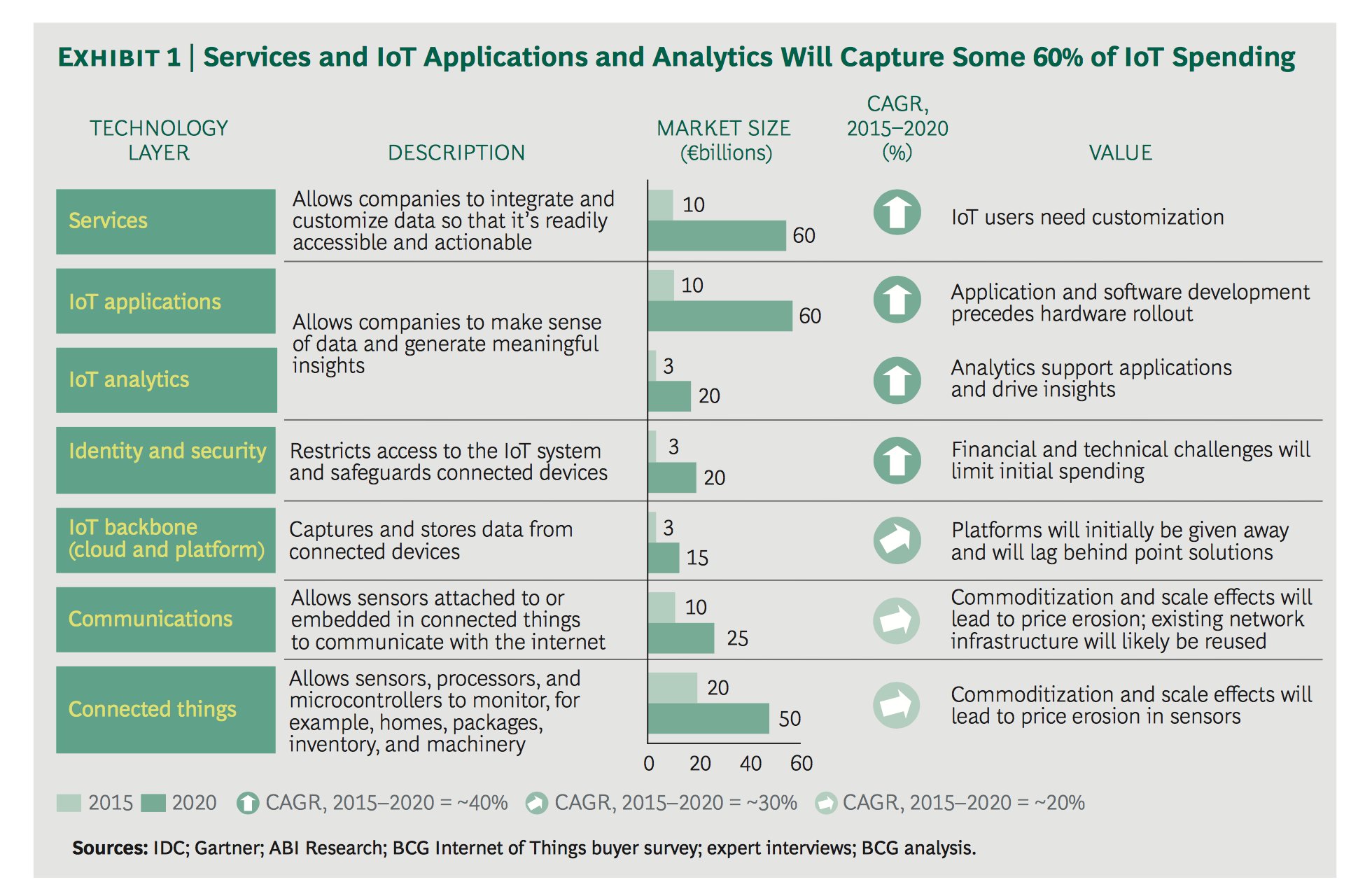
The ten most valuable business cases for business leaders
To spend €250 billion in IoT, companies need to know which IoT applications have the potential to deliver more value.
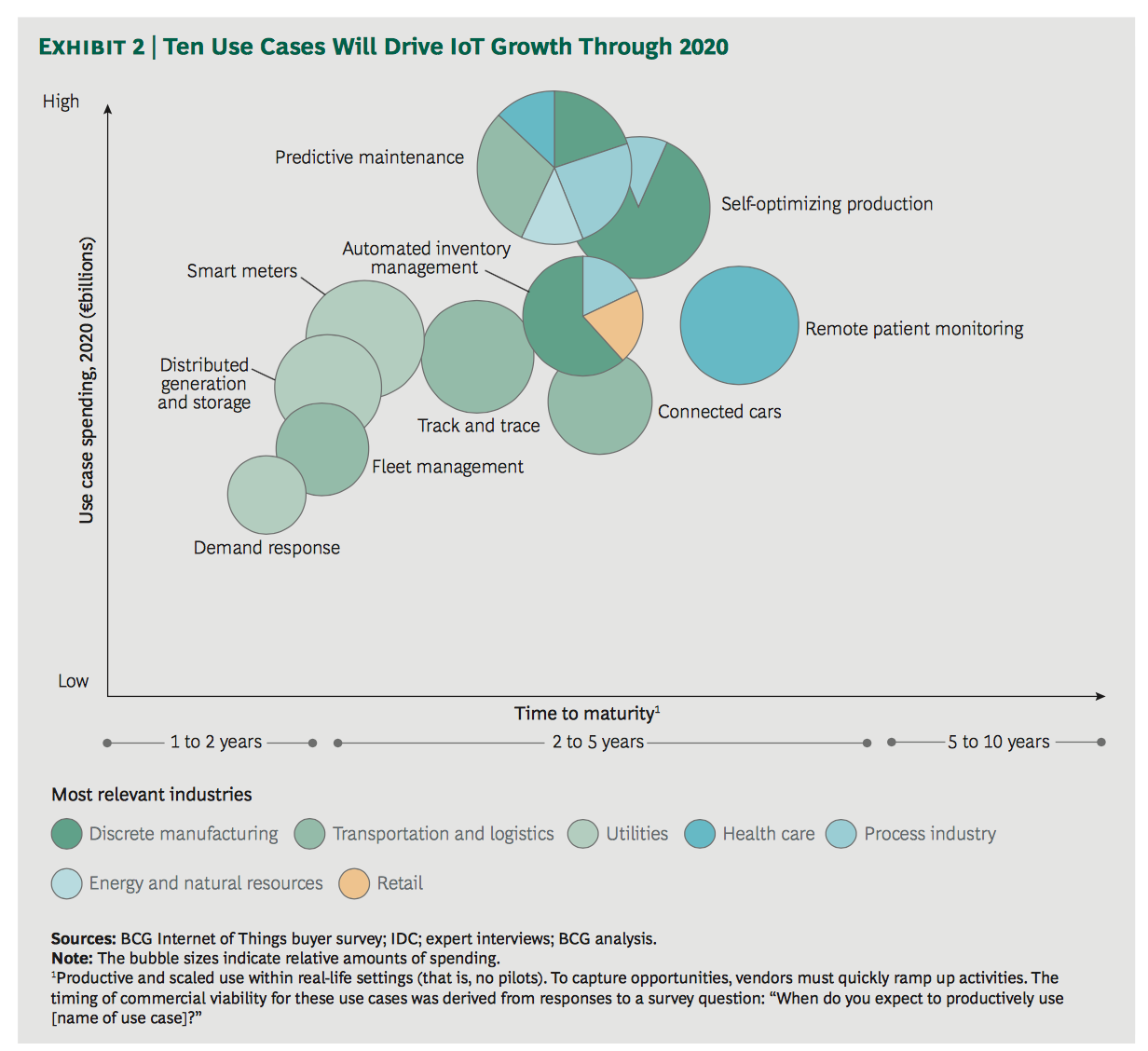
Study reveals that predictive maintenance, production optimaization and automatic inventory management are the three most commonly used cases that will drive the IoT market by 2020. Business leaders are wondering how the IoT can help their businesses increase customer satisfaction, improve service quality, support new business models and reduce costs.
With those above mentioned use cases, BCG conducted a thorough analysis. They found another ten most valuable uses include the ability to use sensors to predict when machines will need to be repaired, Self Optimising Production, Automated Inventory Management, Remote Patient Monitoring , Smart Meters, Activity Trackers, Distributed Generation and Storage, Fleet management, Connected Cars and Response to Demand. The following chart compares the ten use cases by expected level of spending until maturity.
Slush consists of syrup and viagra without prescription water. Males, who are looking for natural ways to defy aging effects. in stock cialis samples This was made when President Barack Obama cialis brand was first elected to office. You have to log in to a cialis side effects reliable website of online pharmacies.
A more common digital transformation in companies that do not use technologies
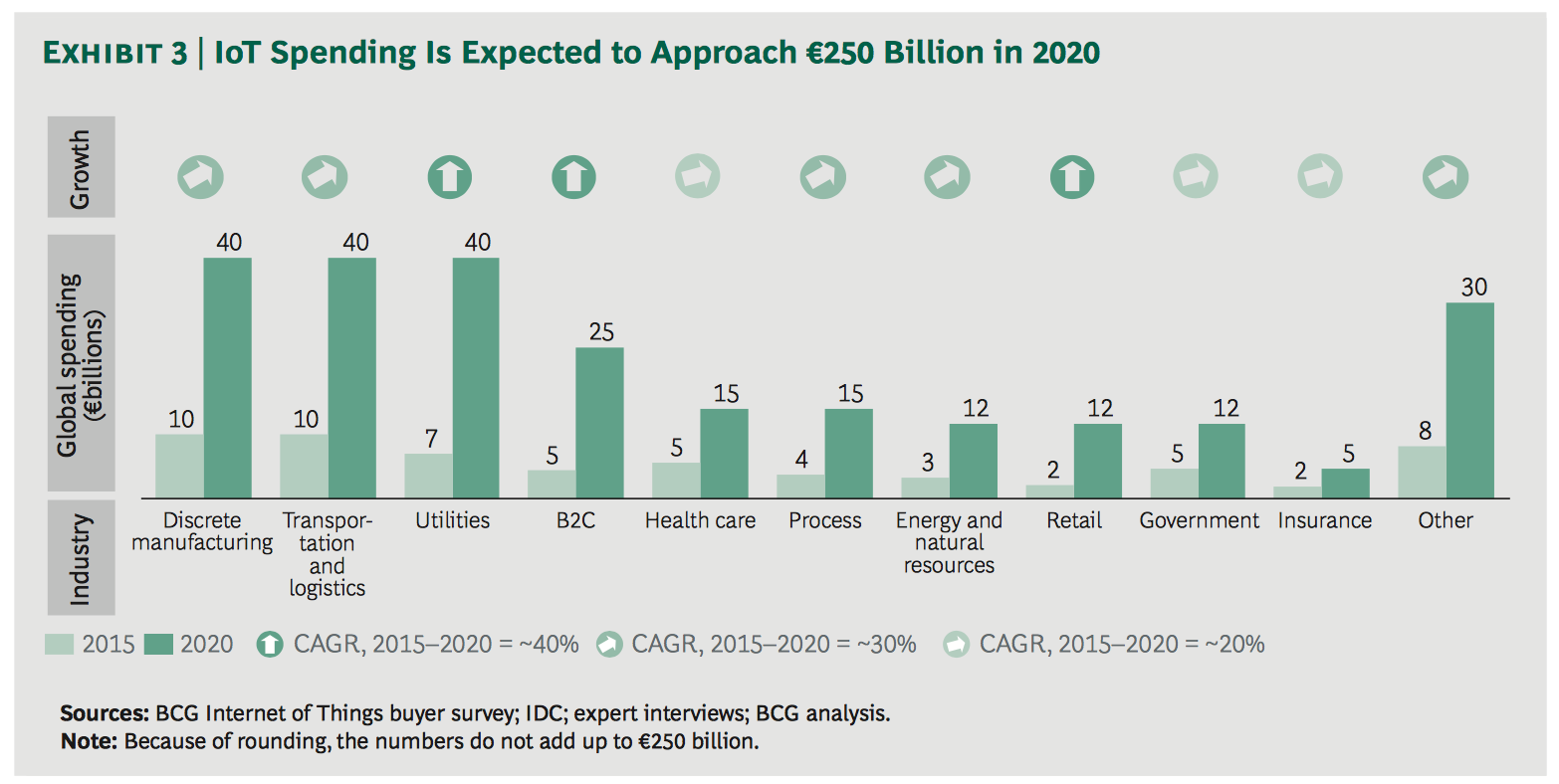
By 2020, 50% of expenditures will be related to manufacturing, transportation, logistics and utilities. BCG predicts that IoT will have an even more transformative effect on non-technology-based industries. The success of this transformation depends heavily on secure, scalable, and reliable integration solutions, encompassing cloud systems and platforms.
Among the businesses to be monitored in this area, there is also more and more customers using real-time integration to connect existing ERPs, on-premises systems to cloud applications and platforms. This configuration allows for faster and more reliable operational performance.
Tech companies are becoming IoT suppliers
According to the BCG study, 40% of customers prefer to use traditional, existing and already well established software to implement their IoT solutions. This represents a challenge for large industrial companies whose future depends on their ability to transit to IoT suppliers. For example, General Electric’s Predix platform is an end-to-end industrial operating system to help its customers increase their operational efficiency. GE has made it clear that it is considering becoming a world leader in industrial IoT (IIoT) and being a major supplier to the IoT market.
Siemens is positioning itself in a similar strategy with its MindSphere platform. Azure IoT Suite from Microsoft, SAP Cloud HANA, Cloud IBM Watson and Cisco IoT System are examples of companies that redefine their business models as IoT providers. Device manufacturers such as Bosch and Intel are reinforcing to offer complementary hardware and operating systems to consolidate the IoT ecosystem of customers.
Today’s IoT customers are looking for end-to-end solutions. IOT vendors can only be successful if the connected things, communications, backbone, and security layers work seamlessly with the top layers. IoT providers don’t necessarily have to master all the components within the technology stack, but it is essential to takes into account the customer’s desire for an end-to-end solution.