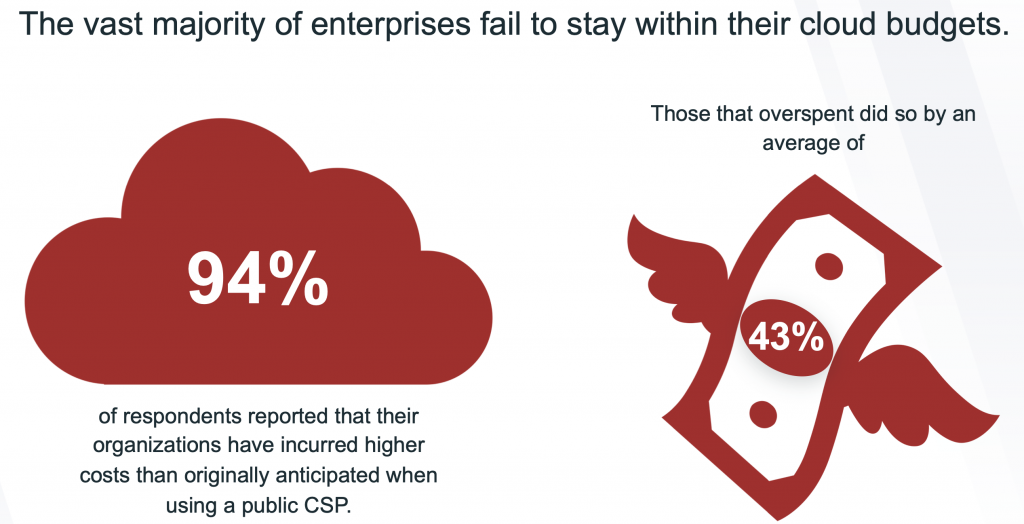
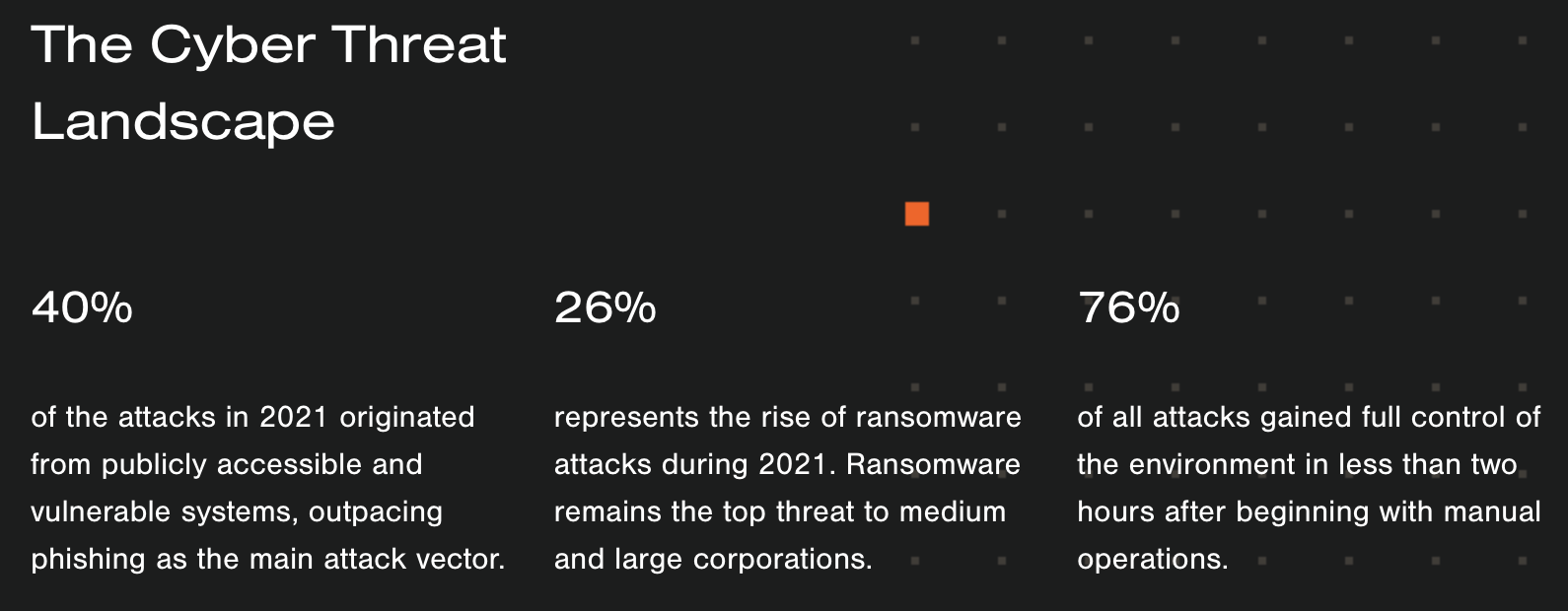
Data as a Service: Enterprise search benefits from Artificial Intelligence and Machine Learning
According to IDC, data as a service, voice-controlled apps, and AI-based services are the most important IT trends of the coming years. Data marketing and data analysis are among the most important challenges for companies. IDC expects that the amount of data created in 2023 will reach over 100ZB, one trillion gigabytes), most organizations also need to turn to external data in order to execute a variety of business processes. This translates into more than 90% of large companies generating their revenue from data as a service.

This is the provision of information and distribution of data for customers. AI-based services and machine learning methods help to interpret data and are therefore becoming increasingly important. In the future, digital services or apps will hardly be able to keep up with the market without the support of artificial intelligence. Artificial intelligence (AI) is a driving force behind digital transformation, encompassing innovations such as machine learning, natural language processing (NLP), data labeling platforms, and predictive analytics. According to IBM 35% of companies report using AI in their business, and an additional 42% of respondents say they are exploring AI.
The latest report by Research and Markets also shows that AI is expected to achieve a compound annual growth rate of 52% by 2025, indicating its rapid adoption by global businesses. The global AI spending reached over $55 billion in 2021 (IDC) and the AI market is expected to grow to $1.81 trillion by 2030 (GrandViewResearch). By 2023, 60% of all digitization projects will be supported by artificial intelligence functions and almost half of all apps will be voice controlled. One survey also found that 87% of global organizations believe that AI technologies will give them a competitive edge.
The majority of companies are using machine learning processes in marketing & sales, healthcare, banking, manufacturing, and retail sectors. The machine processing of language is becoming increasingly important. Self-learning systems that process complex amounts of data in real time are also gaining importance. AI-based systems are expected to take on more and more tasks and relieve entire departments.
The benefits from artificial intelligence and machine learning are numerous:
- 42% of companies stated that the profitability of their ML and AI initiatives exceeded their expectations, while only 1% said it didn’t meet expectations. (Accenture)
- By 2025, 50% of companies will have devised AI orchestration platforms to operationalize AI, up from fewer than 10% in 2020.Gartner
- Global machine learning as a service (MLaaS) is currently used mostly in healthcare and life sciences, but it is expected to grow in industries including manufacturing, retail, telecom, finance, energy and utilities, education, and the government.
- 92.1% of companies state they are achieving returns on their data and AI investments. (NewVantage Partners)
- AI-powered enterprises will be able to respond 50% faster to customers, competitors, regulators, and partners than their peers. (Oracle)
- AI and machine learning will contribute to the labor productivity increase by up to 37% by 2025. Industry, Research and Energy (ITRE),
- 27% of the respondents of the latest McKinsey Global Survey on AI report at least 5% of earnings before interest and taxes attributable to machine learning-based AI.
- PwC research shows that the global GDP could be up to 14% higher in 2030 (up to $15.7 trillion1 to the global economy) as a result of the ML and AI accelerated development and take-up. (PwC)
- According to PwC research, 45% of total economic gains by 2030 will be the result of AI-driven product enhancement, stimulating consumer demand.
- IBM’s new cognitive phishing detection capability uses machine learning to help businesses detect a phishing site up to 250% faster than traditional methods.