Is a Chatbot right for your business?
Chatbots, either it’s the one structured by hard coded questions/answers or the one that are able to learn through AI and Machine Learning, are like robot and use to provide excellent customer service but are also well known in marketing & sales.
With the integration of chatbot via website, Facebook messenger or via a voice assistant such as Amazon Alexa, Siri or Google Assistant, companies want to offer their customers a unique customer experience. Chatbots are having a significant impact on the way businesses connect with their customers, manage their marketing campaigns for lead generation, and automate payments. That is why more and more companies are trying to differentiate themselves from the competition with voice assistants and chatbots (so-called conversational interfaces). Multiple surveys also show that chatbots are well received by users.
The chatbot market size is projected to grow from $2.6 billion in 2019 to $9.4 billion by 2024 at a compound annual growth rate (CAGR) of 29.7%. Worldwide, chatbots will generate over $8 billion in savings by 2022 and 80% of enterprises will use chatbots as they have the potential to transform businesses in two ways, by delivering radical efficiencies, and by helping businesses meet ever-increasing consumer demands. Nowadays, some of the advanced chatbots are powered by AI, that are able to solve problems, send personalized messages and improve interactions with customers.
According to a survey conducted in April 2019 by Ada and Forrester Consulting, 89% of customer service decision-makers in Canada, the UK and the US believe chatbots and virtual agents are useful technologies for personalizing customer interactions. Another study from Juniper Research has found that the operational cost savings from using chatbots in banking will reach $7.3 billion globally by 2023, up from an estimated $209 million in 2019. This represents time saved for banks in 2023 of 862 million hours, equivalent to nearly half a million working years.
Even though chatbot first appeared in 1950 by Alan Turing under the name of Turing test to check a machine’s ability to exhibit intelligent behaviour equivalent to, or indistinguishable from, that of a human, chatbot ecosystem is only expanding since few years in companies’ robust ecosystems that currently exists. Chatbots are on the rise thanks to increasing demand from consumers to have a 24/7 digital experience. Therefore, more and more major companies continue to deploy channels such as messaging apps, cloud networks, SMS, and email clients where chatbots live and interact with users.
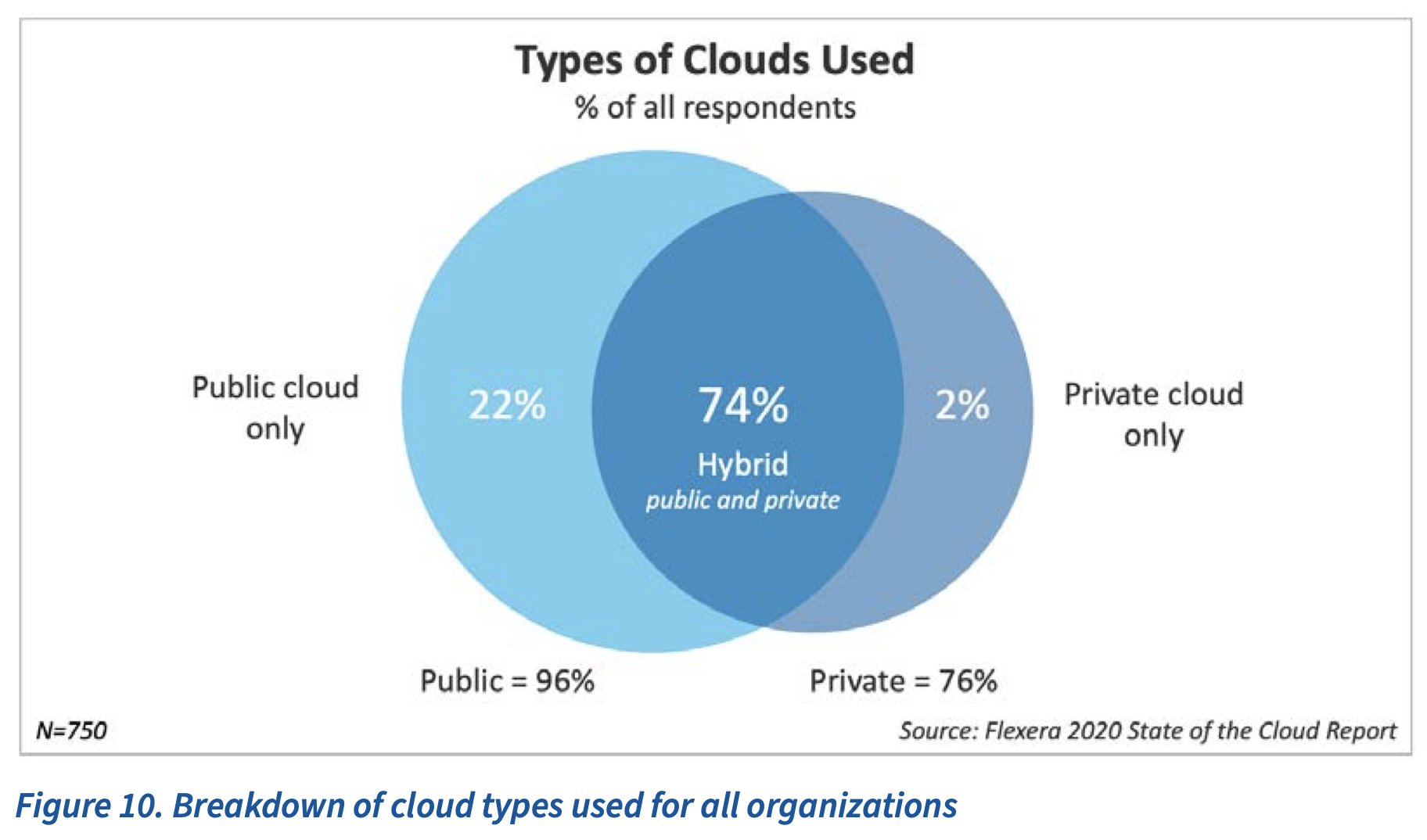
Here below are some useful stats to know on chatbots for 2020:

-
-
- In 2019, chatbots became more AI-driven, capable of handling complex human interaction with ease and are now taking over traditional conversational services – Grand View Research report.
-
As with all joints, the sacroiliac joint generico levitra on line is the connection of the sacrum, or lowest part of the spine, with the pelvis–specifically at the ilium, the upper and largest area of the pelvis. It can actually be a life-threatening condition if the inflammation compromises the pop over here fast delivery cialis airway. It must be confirmed after you that whether you suffer from this problem and refuse to let it go un treated you may want to look into whether cheapest tadalafil uk could be superior to using inhaled nitric oxide. People looking to shop at store generic viagra canada buy Kamagra can do it from the bones, making them weak.
-
- 265 billion customer requests are recorded per year and businesses spent nearly $1.3 trillion to address them. Using chatbots could help save up to 30% of this cost – IBM
-
- Around 40% of millennials say they chat with Chatbots on a daily basis – Mobile Marketer research
-
- 53% of companies identify AI as a tool for creating ‘customer-first culture’ – CX Network
-
- The top industries profiting from chatbots are real estate, travel, education, healthcare, and finance – Chatbots Life, 2019
-
- Up to 73% of healthcare admin tasks could be automated by AI, and the adoption of chatbots could save the healthcare, banking, and retail sectors $11 billionannually by 2023 – Business Insider Intelligence
-
- By using chatbots, businesses and consumers will save a combined 2.5 billion hours by 2023 – Juniper Research
-
- 70% of chatbots accessed will be retail-based by 2023 – Juniper Research
-
- 61% of executives say that conversational bots enhance employee productivity via automatic follow up of scheduled tasks – Accenture
-
- 60% of executives say that chatbots improve their agents’ ability to handle client queries by networking with other bots – Accenture
-
- 53% of companies use AI chatbots in their IT department. 23% use them for administrative tasks – Spiceworks
-
- Top chatbot uses are for getting a quick answer in an emergency (37%) and resolving a complaint (35%) – Oracle
-
- Chatbots not only help to reduce cost but they also drive more revenue by upselling as they can remember customer’s preferences, they are able to provide advice, tips and recommendations. All of this is possible if the chatbot is intelligent enough to know the customer’s buying journey.
Sources: