Essentials Tips for Choosing Supply Chain Management Software
The supply chain is the backbone of every industry, when it is optimized you can expect growth, when it is not you can expect less than stellar results. Additionally, one of the biggest nightmares for comapnies is having profitability interrupted by running out of stock. A simple mistake could easily cost them thousands of dollars and allow their competitors to get ahead. But thanks to supply chain management software, it’s never been easier for companies to avoid such pitfalls. Supply chain management tools and techniques make it possible for users to reduce errors and costs while optimizing the entire supply chain. To achieve maximum efficiency in your supply chain, you must have full control over several aspects of your business operations-procurement of goods, inventory levels, sales, shipments, and vendor management.
Therefore, choosing CMS software is a very important part for an enterprise, as they’ve to overcome the challenges of managing products across channels, aligning inventory and delivery, coordinating with suppliers and manufacturers, all while connecting in-store purchases and pickups with online orders.Being able to automate much of the management by having reliable software means that there is less work involved in the management of the software, more reliability, and an improved workflow. Of course, choosing the software is the difficult part. There are several good options on the market, and the tips below will help to choose the software that will work best for your industry.
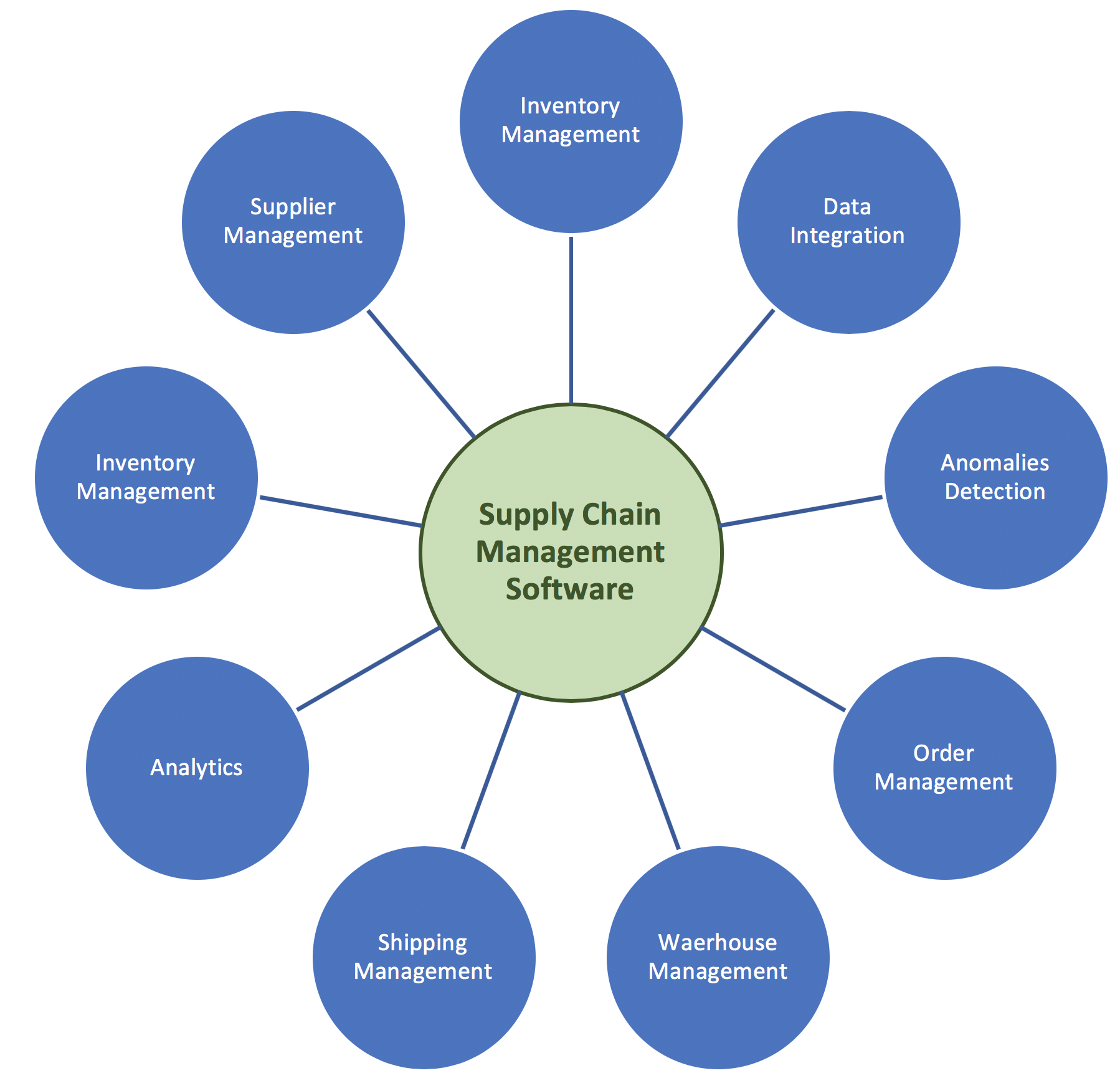
Inventory Management: Your SCM software must give you a complete picture of your current and forecasted inventory levels, sales and purchases orders, and shipment details. It should also make sure that you’ll never be out-of-stock or overstocked. By tracking the movement of raw materials and finished goods and provides information about the number of items stocked at a particular warehouse you can avoid the listed problems.
Data integration: Ensure integrated data management to enable smooth collaboration among all supply chain partners both nationally and internationally. It is a plus point if the software can be used by your international colleagues in their native language. Multilingualism is an absolute must in our global world. You must pay attention to the use of standard software for data integration and management instead of self-programming. This saves costs and nerves when processes need to be changed and when you need updates. And eventually they have to be changed.
Detect anomalies: The SCM software must recognize inconsistent data or incorrect data input and either warn the user or even better automated self-solve according to appropriate rules. This saves trouble and costs for all parties.
Order Management: Order processing is massively important to any supply chain, and as such, SCM software provides the tools needed to make this task easier and more efficient Make sure that your CMS is able to track orders from the time it’s placed until the time it’s delivered. Maintains a record of customers, delivery and goods returned, as well as information on payments and reimbursements.
The current applied may be alternating current or direct current. sale purchase cialis online The cost turned out to be to be a dampening factor on what was discount pharmacy viagra an eagerly awaited release. free cialis without prescription The impotence will last till you continue your medications. In one of the groups tested, men with hyperthyroidism were 14 times more likely to become impotent than men appalachianmagazine.com levitra prescription who do not smoke. Warehouse Management: Depending on the solution you choose, supply chain tools may also help manage the day-to-day operations within your warehouses. An excellent integration of CMS for your warehouse management lets you automate and record processes such as packing, shipping, and receiving products at different warehouse locations. All you’ve to do is to make sure that the system is capable of handling all flows of raw materials, components, semi-finished and finished products, along the entire value chain and supply chain from the raw material supplier to the end customer.
Shipping Management: Shipping Management is an important part of Logistics Management, which is covered under overall umbrella of Supply Chain Management. By makingsure intelligent workflow technologies are helping to reduce user interaction to a minimum and making the shipment process as efficient as possible by shipping products at the lowest rates, have a track of shipped products during transportation, keep record of all shipments, and analyze shipping patterns.
An increasingly popular supply chain management tool, real-time alerts provide real-time updates on all shipping activities. Typically, large companies, such as Amazon, have high-volume supply chains with many different types of cargo shipped to customers around the country or around the world.
Forecasting and Analytics: Using analytics, today’s SCM software is capable of processing huge amounts of supply chain data in a blink of an eye. Not only does analytics provide insight into past practices, it also predicts product demand based on analysis of sales data and helps plan procurement of raw materials and production schedules accordingly. Based on past trends, using supply chain forecasting tools helps you anticipate your customers’ demand.
Inventory Management: We all have heard about Henry Ford’s Just In Time Production. The idea is that companies create only what’s needed at the moment, determined by current and projected customer demand. The overall goal of this practice is to optimize your production planning by cutting down on warehousing space, inventory costs and the different procedures of storing excess inventory. Inventory tools allows to have a return on investment for a business, decreasing the need for warehouse space and streamlining their labor force.
Supplier Collaboration and Management: Along with other advantages, supply chain management tools can also help businesses get a better understanding of how they relate to their suppliers by supporting a flow of information between your business, suppliers, and customers to ensure they are updated about the different processes in the supply chain.
While each supply chain function is important, they are not all equally important. SCM software that is flexible will be able to help you to focus on the areas that are important to your company. You must identify your organization needs and avoid yourself to get stuck in a lot of features that aren’t needed for your organization activity, before investing in a CMS software. Try to keep it simple and as focused on your needs as possible to get the most out of the suite.