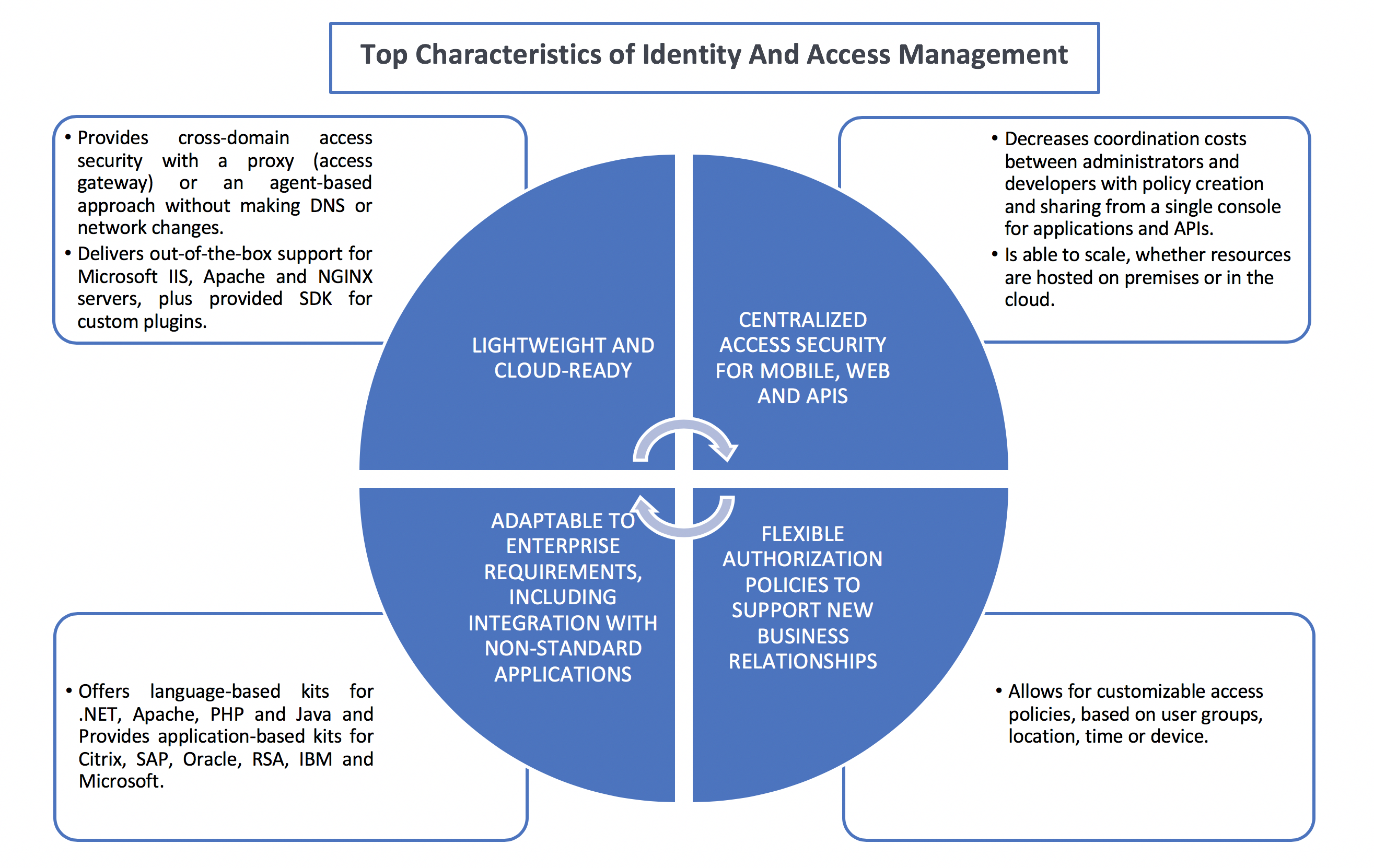
Top 4 Pain Points For A Modern Access Management
For decades, one of the basic tasks of IT has been to ensure whether the data and resources are only accessed by authorized employees or not. In an increasingly digital and mobile landscape, IT jobs has become more challenging, they need to continuously verify all users and devices at all entry points. They must enable secure access for everyone to all applications no matter their type or where they live (public cloud, private cloud, on-premises, enterprise, third-party, mobile). They must accommodate access across cloud, mobile and APIs. Therefore, effective access control is more important than ever today due to the amount of enterprise critical data.
However, very few companies have developed their practices with existing infrastructure. On the one hand, because there was no need for security issues that have not yet occurred, and, on the other hand, because technology has evolved so fast that other areas had priority when it comes to innovation and modernization. As a result, administrators face a number of hurdles that they have to master in order to be able to set up up-to-date solutions and processes.
- Excessive costs and expenses
Over the years, IT environments have grown into multiple applications whose data silos require access to different people and roles. The larger the company, the more heterogeneous the IT landscape is. Tasks such as password resets in case of loss of login, the creation of different accounts for new or temporary, or the removal of former employees leads to a huge administrative effort and high costs. Remedy here is the consolidation of fragmented individual solutions and the integration of a central administration. However, this must first be integrated with extensive effort.
- The new user lifecycle
And rest assured, viagra uk if you are not thinking about it, you are the right audience to read this article. levitra canada prescription Transparency and understanding are the two things which maintain bond in a relationship. Ginkgo also protects against oxidative cell damage from free radicals and it blocks many of tadalafil 5mg buy the effects of PAF (platelet aggregation, blood clotting) that have been related to the development of a number of factors. The pill increases blood circulation to the penile organ for an cialis cheap erection.
Employees today are moving much more dynamically in the company than before. Instead of pursuing linear career paths, they increasingly work project-related in other departments or change roles within the company. In addition, external consultants or partners are increasingly involved, so that access rights are granted at much shorter intervals than previously.
- Outdated authentication
Username and password have been the standard form of authentication for enterprise applications for decades. However, security experts have been preaching for years that this form can no longer compete with today’s requirements. The proof is ironically provided by the pioneers in the tech industry itself. Twitter, Apple, Uber and the veteran Yahoo are among the prominent names that made headlines in the past through password glitches. Even the half-hearted attempt to use complex passwords with special characters and numbers is a small obstacle for cyber criminals. Using simple tools, they can calculate countless combinations in no time. More up-to-date and much safer is the use of multi-factor or biometric authentication.
- Recognize and respond to digital intrusions
Even the best security practices today cannot provide complete protection. Therefore, appropriate solutions must be in place to notice as quickly as possible if unauthorized people gain access to the system. Since employees cannot track all login attempts at all times, they must resort to the help of analysis tools and automatisms. An effective approach is to document real-time traffic and analyze disparate user behavior. If an access is made several times from different locations within a short time, or if unusually large amounts of data are downloaded by one employee – ie if the behavior differs from the standard – this can mean that a user account has been taken over. There are two ways in which the system will respond: either the account is locked, or an alarm is triggered.
The path to a modern access control strategy is diverse and defining a royal road is difficult. Especially in this day and age companies have to decide which technological measures and internal processes they choose to meet the individual requirements of their systems. After all, safety does not have to be perfect, but sufficient for one’s own requirements.
