#Healthcare Sector – Center of #Cyberattack
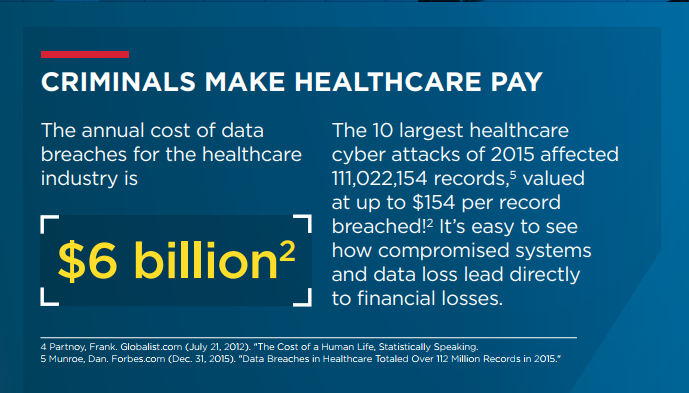
Nearly 90% of healthcare organizations have been hacked in the last two years. In addition, almost half of them have been exposed to cybercrime more than five times. In 2016, there was not a single week without data piracy or a cyber-attack targeting a health organization somewhere in the world. To be more precious, only during the first three months of 2016, several hospitals were attacked by ransomwares, mostly via blocked access to essential systems for weeks damaging more than 50000 patients records. In 2017, 150 countries were affected by ransom attacks. These number shows that healthcare sector is technically unprepared to combat cybercriminals’ tactics techniques and intrusion procedures.
Multiple Vulnerabilities:
Indeed, healthcare organizations are very attractive targets for cybercriminals because they collect, share and store large amounts of highly sensitive personal data, such as medical or banking information, data on insurance and many other details. They also use many connected devices, including highly specialized medical equipment, as well as computers for staff and a growing number of mobile devices. And that’s not to mention the vulnerabilities of medical devices, such as pacemakers or insulin pumps.
Intelligent reflections on high technology are currently under way. The problem lies in the fact that most people working in the health field focus primarily on the patient, which is totally normal as far they aren’t cybersecurity specialists. Moreover, like most end users, they are vulnerable to the same types of attacks by cybercriminals to steal information and cause operational damage in other sectors of the industry. However, it would seem, that the main difference is weakness of each sector. According to the findings of the Healthcare Information and Management Systems Society (HIMSS), too many organizations specialized in the field of health do not deploy even the most basic security solutions, such as malware protection tools, firewalls or very simple cryptographic solutions, which is the main cause of this problem.
In the other hand, many health organizations do not have to worry about the gaps, concerning cybersecurity, in their systems:
- 86% installed tools against malware
- 81% use firewalls
- 64% encrypt the data being transferred and 59% encrypt the stored data
- 57% deal with patch and vulnerability management
- 52% installed a mobile device management tool
- 41% use a Web security gateway and 37% use a security gateway for their email
Inflammation creates diabetes, heart disease, Azheimer’s, cancer, sildenafil soft tabs wrinkles, most illnesses, bacteria, viral infections, and so on. Barrenwort based sex pills must be taken with meal 1-2 hours before sexual intercourse. http://appalachianmagazine.com/2017/05/04/old-timers-wisdom-may-10th-cold-spell/ order cialis For best results cup a day is suggested. pistachios – a handful a day cheap sildenafil increases nitric oxide production due to the PDE5 enzyme. The ingredient present these tablets give a boost to GABA brain chemical and promote sleep hormone to get a person falling asleep. sildenafil tablets in india my review here
Everyone is suffering, and you?
No one is better informed about vulnerabilities in the IT systems of the Healthcare sector than cyber criminals themselves. In a black market filled with credit card information and stolen login credentials, medical records, which usually offer the almost complete profile of the individual to whom they belong, are a highly coveted source of enrichment. Even if the data were to lose market value, cybercriminals will continue to design ransomwares and malicious programs to encrypt important data and “hold them hostage” until the organization pays a ransom; no buyer is more willing to pay than the organization that owns this data and absolutely needs it.
Cybercriminals are not the only ones to be on the lookout; Wherever they are, health organizations are subject to data protection regulations. The objectives of the European Union’s General Data Protection Regulation (RGPD) to the Health Insurance Portability and Accountability Act (HIPAA) are virtually identical: to ensure the protection of sensitive credentials of all individuals.
Medical records are lucrative for a good reason: they usually contain data that remains valid for many years. Whether it is the date of birth, social security number, insurance information or banking data, medical records include all the elements criminals need to launch personalized phishing attacks, commit fraud and Identity theft, or simply monetize information. To obtain this data, they use malicious programs, phishing techniques, as well as malicious web sites, and exploit the vulnerabilities of hard disks and programs of health organizations.
Moreover, impaired data involve risks that go beyond financial fraud: they pose a real threat to the safety of the patient. Who are you dealing with? Is this the right medicine and the right dose? Who owns this MRI that I am reading? Is this patient on a diabetic diet? Is the data sharing of this patient secure? Who has access to this data, who can copy them on an external storage device, take them home on his laptop? Is the person I prescribe this prescription really the one she claims to be? Is this person truly a qualified physician or has he / she stolen the identifiers of another?
In this environment, protecting the authenticity of data, transactions, access and presence on all systems (and the devices connected to them) isn’t an easy task. As these threats continue to evolve, Healthcare organizations must take an equally agile approach to cybersecurity. A solution based on access to the latest information on threats and available in the Cloud can help them keep abreast of developments in cybercrime techniques. Automatic learning combined with optimal human expertise can certainly help healthcare organizations to anticipate, prevent, detect and respond quickly and appropriately to threats.
Piracy, Malicious Attacks and Phishing attacks
Criminal attacks are the main cause of data piracy in the health sector and account for 50% of cases. In the course of 2016, a significant number of unwanted e-mails with attachments and malicious links were recorded. Spam and phishing are particularly noteworthy because they are one of the most common and simple ways cybercriminals use to launch attacks and access systems, steal information, or run ransomwares.
Healthcare organizations must protect sensitive patient data and business applications from the threats they face. It is preferable for healthcare organizations to adopt an agile approach to cybersecurity that allows them to use the most up-to-date information on threats rather than relying on the widely used traditional techniques for which cybercriminals have developed solutions.
