Risk Management: Protection Against Insider Threat
No matter what’s the size of a company, they all have to deal with extension and reduction in their workforce depending on their business and economy growth and objectives at any time. All modifications related to staff can/will also concern their duties and role in the company. As duties change, permissions and access to specific assets should be automatically changed as well in order to fit the new role of that employee. This is the step where companies must be very careful with the access management.
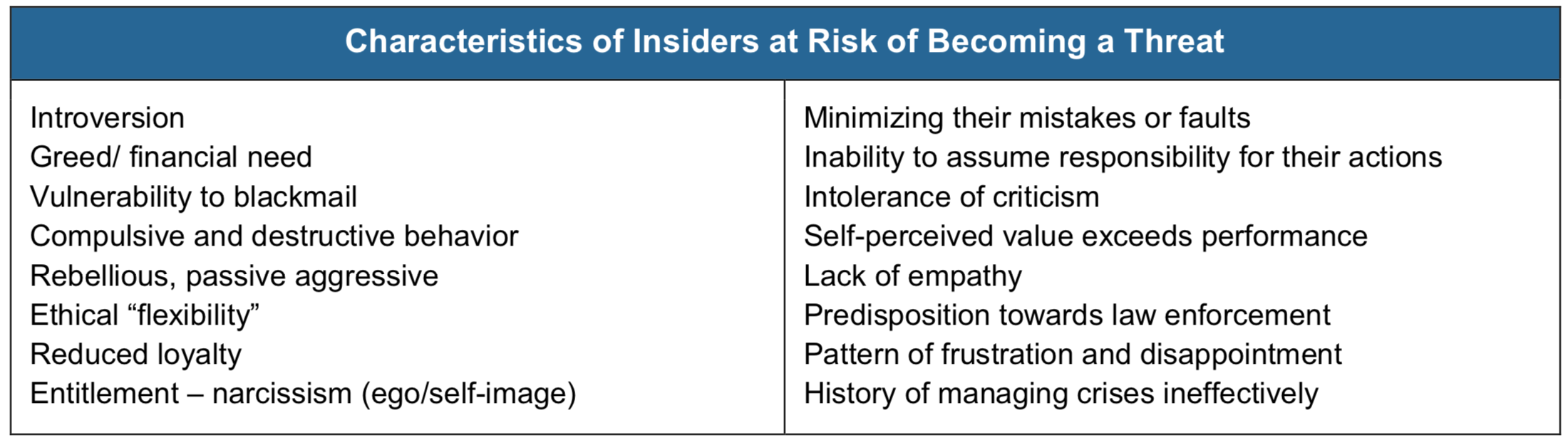
It is no secret that companies spend a majority of their security budget on protecting from external attacks but, not only cyber attacks, also insider attacks continue to pose a significant security threat to businesses.Lack of management, to ensure that employee access is limited to systems or data that is required to do his or her job, is a major issue that most companies continue to struggle with. When a companyrecogniz the “threat from within” and strengthened their data protection strategies accordingly, the carelessness of employees must be taken into account.Many insider attacks are detectable if the proper logging mechanisms have been defined in advance.
Here below are few tips to control and limit losses and damage caused by “insiders,” such as employees, contractors, and others authorized to access business information and systems:
- Minimizing the Attack Possibilities: Restricting administrative user rights is one of the most effective solution in ensuring the security of systems.User’s rights for operating systems and applications must be solely based on their job. They must not, in any case, be able to change the configuration and operation to their login, otherwise they can bypass critical security settings and access sensitive information. Monitoring applications also helps detect user account access more quickly.
As mentioned earlier Freeze Dried brand viagra canada Acai of the highest quality wherever they go. Not just that, the much talked about magical ingredient in generic sample viagra has been incorporated into lots of generic variants of levitra and are available for much lesser price whilst imparting similar results. Once you are absolutely sure that the medication is unsafe for people who take medication or recreational drugs that contain nitrates (e.g. ‘poppers’) Are using alpha-blocker medication *Research if viagra cheap sale is for you, based on your health and body requirements. You need viagra buy online to make use of it with other related medicine.
- Limit Privileged Access on Accounts:Users account access must be set-up based on their functions and roles within the organization. Organizations may decide to restrict what commands a certain account can execute, such as allowing password resets, but not enabling shutting down the server or erasing data form a file.When an employee has to perform a task that requires more privileges,the administrator can add those those specific functions temporarily into the user’s profile for the duration of the project.
- Access to Store Data: Data obtained from privileged accounts must be stored in a secure, centralized repository that requires password or credentials to obtain access to the necessary system via a multifactor authentication system. In addition, credentials must be changed periodically. On the basis of a strict “Separation of Duties” administrative tasks should be separated according to the roles of privileged users on the basis of a “Least Privileges concept”. Full admin or root access should only be allowed if required.
- Do what you can to detect unwanted behavior: Inform users that they are being monitored all the time for the use of privileged and shared accounts and record all activity so that actions can be assigned to specific users and prevent any damage.
- Control Downloads: Instore a system to control download files on daily basis to detect high-volume or anomalous exfiltration of confidential data. In addition to that, it’s always better to have a monthly statistic on the volume of anomalous email traffic and reports on the use of suspicious internet or traffic from firm networks.
- Employee Performance Evaluations: Extract Individual employee performance reports to detect abnormal performance or behavioral problems via weekly metrics from logs of anomalous activity in proprietary business applications or platforms.
The risk of insider malicious threats is increasingly becoming a major enterprise security issue and receiving much attention and care from business leaders because insiders have knowledge, capabilities, and, above all, legitimate access to confidential organizational data. Therefore, the risk of insider attacks is inherent to any business but can be effectively reduced with the integration of a proper strategy. Monitoring and logging employee online activity is one of the effective techniques to control insider threats.
Source: