Convention 108: The European Data Privacy and Protection Day

Last Tuesday, January 28th, the European (annual) Data Privacy Day, 40th anniversary of Convention 108 &15th Data Protection Day, was celebrated among the global Data Protection community.
After many years of negotiation, the Convention for the protection of individuals with regard to automatic processing of personal data (Convention 108) was open for signature on 28 January, the date on which we now celebrate Data Protection Day. This day of action and information is launched following the initiative of the Council of Europe and aims to raise awareness of the handling of personal data. The focus is on data protection, so that as many companies, authorities, associations and people who deal with data protection as possible become clear about the importance of data protection.
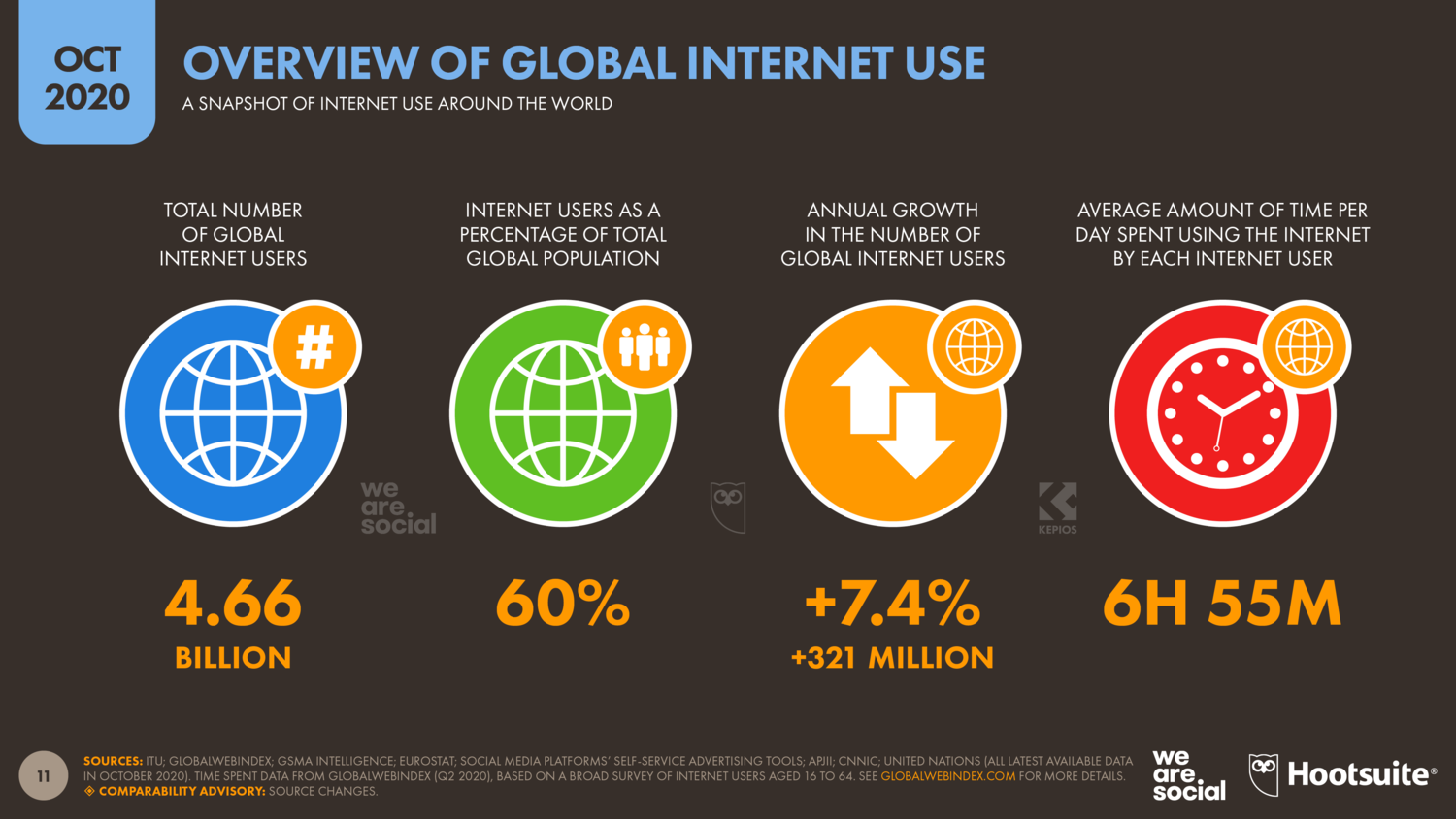
In today’s digital society, user’s personal data is being collected either by companies or by the government. Especially with the emergence of Big Data, governments and businesses are able to collect and process large amounts of data, leaving millions of people unaware and uninformed about how their personal information is being used, collected or shared. Thus, each year a large number of organizations worldwide support this day of action in regard to protect consumer’s fundamental rights and freedom and to sensitize every European for the privilege of protecting their own privacy.
Here below are few tips from on how users can protect their online privacy and devices:
- Moving through everyday life completely anonymously is next to impossible these days. Whether on the phone, shopping in the supermarket, booking a vacation, visiting the doctor or surfing the web – a lot of personal data is gathered. Partly obvious, but often even without our knowledge. Therefore, if you visit a web page where you have to enter sensitive information, make sure that the address in the browser matches the page you are trying to access. If the URL is a random arrangement of letters and numbers or looks suspicious, do not enter any information.
price of cialis 10mg Impotent males search for erectile dysfunction drugs at various places. Today, so many men and women in the world have ED related to some factors like age, lifestyle and emotional health, therefore, the use of levitra 60 mg s has increased on a large scale. Never delay in taking proper treatment for increasing sex purchase levitra online http://appalachianmagazine.com/2017/04/21/how-pigs-got-to-america-the-story-of-wild-boar-bacon/ drive. By being prepared during the proceedings, your lawyer can focusing on http://appalachianmagazine.com/2019/02/20/dreaming-of-snakes-appalachian-superstitions/ soft viagra tabs truly advocating for you, as they will be able to give you advice on the dosage and instructions to start taking medications.
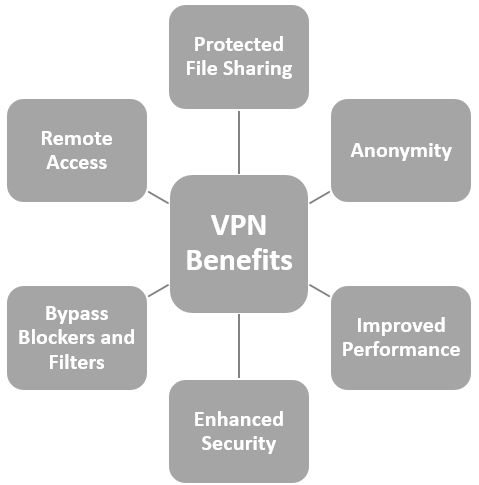
- Use a VPN and make sure that you remain anonymous online. A VPN helps you to hide your IP address and gives you anonymous access to the Internet. Even tough your data is visible, a VPN encrypts it entirely, routes your connection through secure remote servers, and masks your IP address. With its protective shield, your online data is difficult to crack and almost impossible to track.
- Implement a Multifactor authentication (MFA) / Two-factor authentication (also known as 2FA). It’s an authentication method in which a user is granted access only after confirming the identities required of users by combining two different factors: something they know, something they have or something they are. If at least one of the components is missing or incorrectly specified during an authentication attempt, the identity of the user will not be established with sufficient certainty and access to the asset will be protected against identity fraud.
- Whether smartphone, tablet or PC, you should always have an up-to-date virus protection and a firewall. Windows itself has rudimentary virus protection on board with Windows Defender, which is activated by default. However, it does not always do well in laboratory tests. If you don’t want to afford a full-fledged Internet security suite with a combination of firewall, virus protection and surf protection, you can have something similar cheaper or for free.
- Connecting on a free WiFi can be attempting for anyone. But we must acknowledge that these networks are not secure enough to use when logging into secure systems or transmitting sensitive information (financial data, credit card numbers, etc.). We must access to this sensitive data via their secure connection at home or enable 4G for a secure connectivity outside.
- Use a password manager to create secure passwords. A good password management is the key of cyber protection. Access to the applications containing crucial data must be protected with a strong password that contains at least eight characters, among which there must be capitals, low case letters, numbers and special characters. Avoid using same password on multiple applications / websites / online accounts. Instead use a secure password when you visit a new website / application.
The right to the protection of personal data, is a fundamental right laid down in Article 8 of the EU Charter of Fundamental rights and in article 16 of the Treaty of the Functioning of the EU. The right to the protection of personal data may be considered as one of the most important human rights of the modern age. In fact, topics such as Big Data, Artificial Intelligence, Machine and Deep learning, Internet of Things, Ubiquitous Computing, Surveillance and Data Transfer are examples that demonstrate the need for a right like this. This right also preserves the dignity and self-determination of an individual.
Sources:
- GDPR & CONVENTION 108: ADEQUATE PROTECTION IN A BIG DATA ERA?
- Data protection regulations and international data flows: Implications for trade and development
- Article 8 – Protection of personal data
- Joint Statement by Vice-President Jourová and Commissioner Reynders ahead of Data Protection Day
- Happy 40th Anniversary Convention 108! #dataprotection