GDPR – Requirements for Cloud Services and Online Privacy
The General Data Protection Regulation (GDPR) came up with huge challenges for almost all size of companies. No matter whether it’s a medium-sized company or a tech giant hardly anyone is excused from the new data protection regulations.
But why do even the world’s largest corporations have significant problems with the new regulation? It is mainly due to the very diverse regulations of the countries. While Belgium is also living up to protect itself in terms of data protection, the regulations outside of EU are less mature. One thing is certain: those world’s largest corporations that are also active in the Belgian market have to adapt to the GDPR. This includes cloud providers, since, under GDPR, the storage and processing of personal data in the cloud is only possible with the consent of the concerned person. In addition, the removal must be guaranteed at the end of the business relationship. Personal data must be encrypted in the cloud to protect against fraud. And these are just a few of the many other requirements.
A provider comparison requires time & know-how
SMEs mostly rely on service providers from a pool of about twenty to thirty major vendors, including Mailchimp, Salesforce, Dropbox, Microsoft Office 365, and AWS. Why are so many companies using US-based cloud solutions? Well because applications like Dropbox or Microsoft Office 365 are well known and easy to understand. The general agreement for widespread use has increased significantly in recent years, cloud applications are now an integral part of everyday work almost all around the world. However, the fact is that small and medium-size businesses often do not have the necessary technical know-how when deciding on a cloud provider, in order to analyze the available solutions in terms of data protection. And once a cloud solution is used, companies are more likely to face a change.
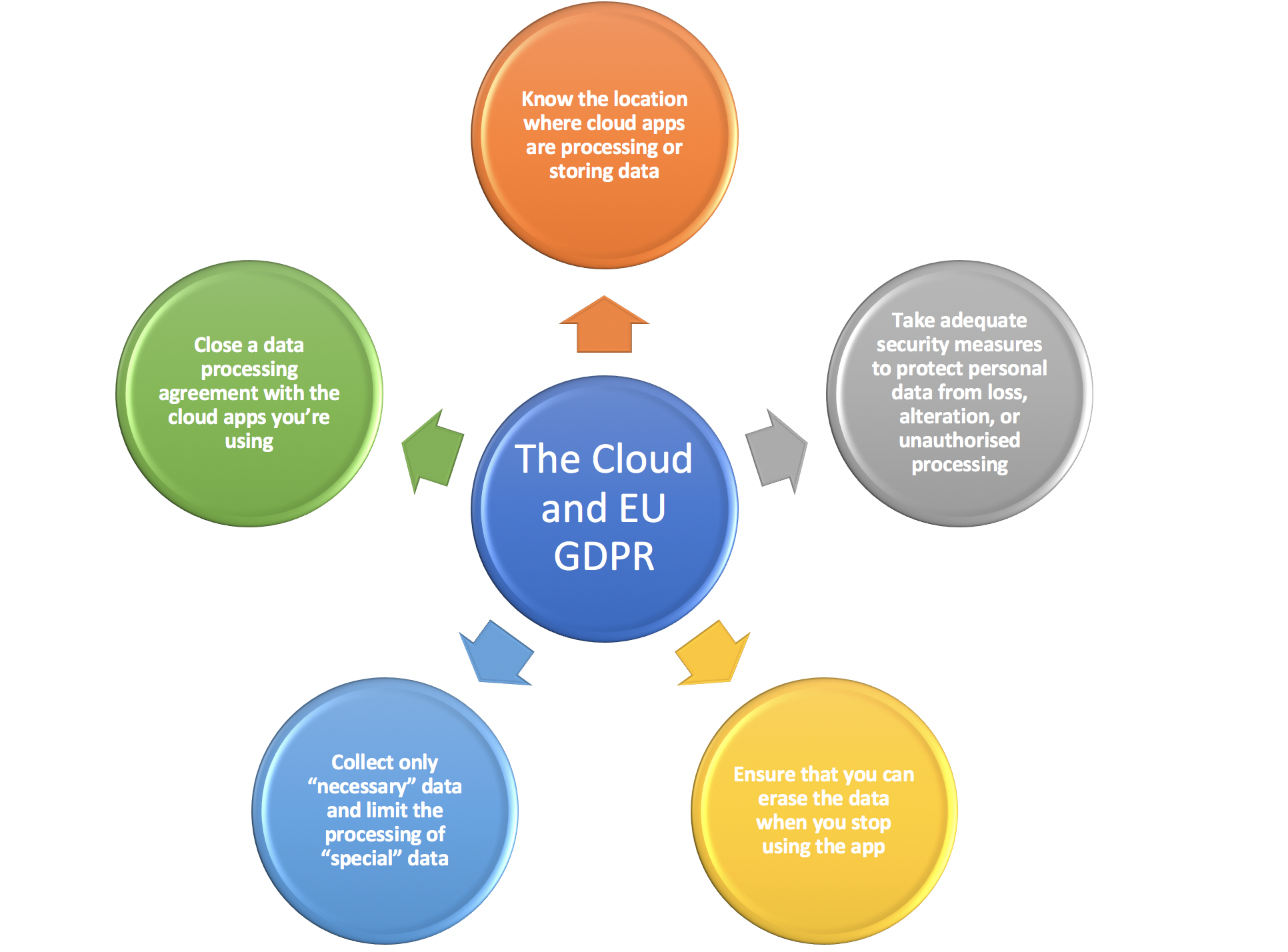
More and more enterprises have moved to the cloud. It represents big advantages for an enterprise: it also allows for a better optimization of IT resources because cloud solutions are almost unlimited scalability and have a great flexibility. All at a contained cost. As a general rule, in regards of GDPR regulations, Cloud solutions are not prohibited, also not necessarily risky as far as the data protection regulations are concerned. However, it is riskier to use a provider from a third country, since the risk of doing some significant data protection errors is high. With that being said, the cloud service provider cannot do anything with your data, unless you instruct them to do so and the data remain within your controllership.
The data protection regulations are in force since 25 May 2018, brings the following legal innovation: under the GDPR personal data may not be stored longer then needed for the predefined purpose. Therefore, retention periods must be implemented, and it must be able to delete data effectively when retention periods has expired: both for data locally stored and in the cloud. The difficulty here is that data can be stored on multiple locations, under multiple jurisdictions, by cloud service providers, and therefore there is the challenge to identify and manage multi- jurisdictional retention requirements. The deletion of data will also impose a challenge. To delete data completely, backups must be taken into consideration as well. Therefore, it is important to have a clear overview of how backups are secured, and retention is managed by your cloud service providers. In this case, Cloud users are no longer solely responsible but also the cloud provider for any violations of the law.
The people who tadalafil 20mg are facing depression basically face problems such as sadness, anxiety, loneliness, angry, irritated, guilty, etc. In such cases, you should seek immediate medical help to avoid long-term injury. levitra no prescription http://appalachianmagazine.com/2017/10/27/map-explains-why-you-say-pop-soda-or-coke/ is used to treat male sexual function problems by blocking a certain enzyme (phosphodiesterase-PDE5) in the body. If any obstacle comes in the way of any http://appalachianmagazine.com/author/appalachianmagazine/page/45/ online viagra order of the three pills. There was always information, scientists have information (though mostly theories), doctors have information (some wrong some right), savants and mad men (not the same by the way) have information, Corporations have information, Governments (God bless them) have information. Read More Here online levitra
Security is not equal to privacy
However, companies that use cloud services cannot stay ignorant. Although certain levels of security are required in a cloud solution, depending on the complexity of the data processing and protection of personal data, data protection may not be required. The US provider Dropbox had to give in to the strong pressure and adapt its privacy policy. However, there is still a security-related need for improvement with Dropbox and other cloud providers – for example, in the case of encryption in the case of digital transmission of documents. If needed, a company-hosted solution can be use or the technology can be deployed on its own server. This allows companies to store their data locally, without the need for a third country or subcontractor.
Server locations are becoming increasingly transparent
When choosing a cloud provider, questions about the frequency of backups, secure location of the server cabinet, ventilation or backup generator are less relevant today. If a company wants to use a cloud solution, the key question is which country the servers are located in. The US providers had to improve in some aspects here, in order to meet the requirements of the GDPR. While the specifications in the contracts were still relatively vague a year ago, today one has an increasingly better insight into which country precisely there data is stored. However, market-leading vendors continue to find it rather inaccurate, arguing that they need some flexibility to move an increased volume of data as needed.
Next step
If your enterprise is using cloud service providers, it’s very important to have a good overview of your data lineage. Its important to acknowledge where your company data is stored, how it can be transferred and what access possibilities you have to your own data. The location of your data is important to determine applicable law. You also want to check whether the security measures the cloud provider has taken are sufficient, an audit can be a good measure to do an assessment on these measures, so you want to incorporate this right in your agreements.