Why Enterprises Must Switch to Windows 10

Many companies are still reluctant to switch from Windows 7 or 8 / 8.1 to the current Windows 10. Because Microsoft has changed its release concept and now brings updates every six months. IT managers fear that they will be overrun by update projects in the future.
But given the announced support end for Windows 7 in 2020, a switch is unescapable. This article explains how an IT organization should proceed once the dice have fallen in favor of Windows 10 – and why you should rely on processes for the “day after” rather than on the LTSB (Long-Term Servicing Branch) version.
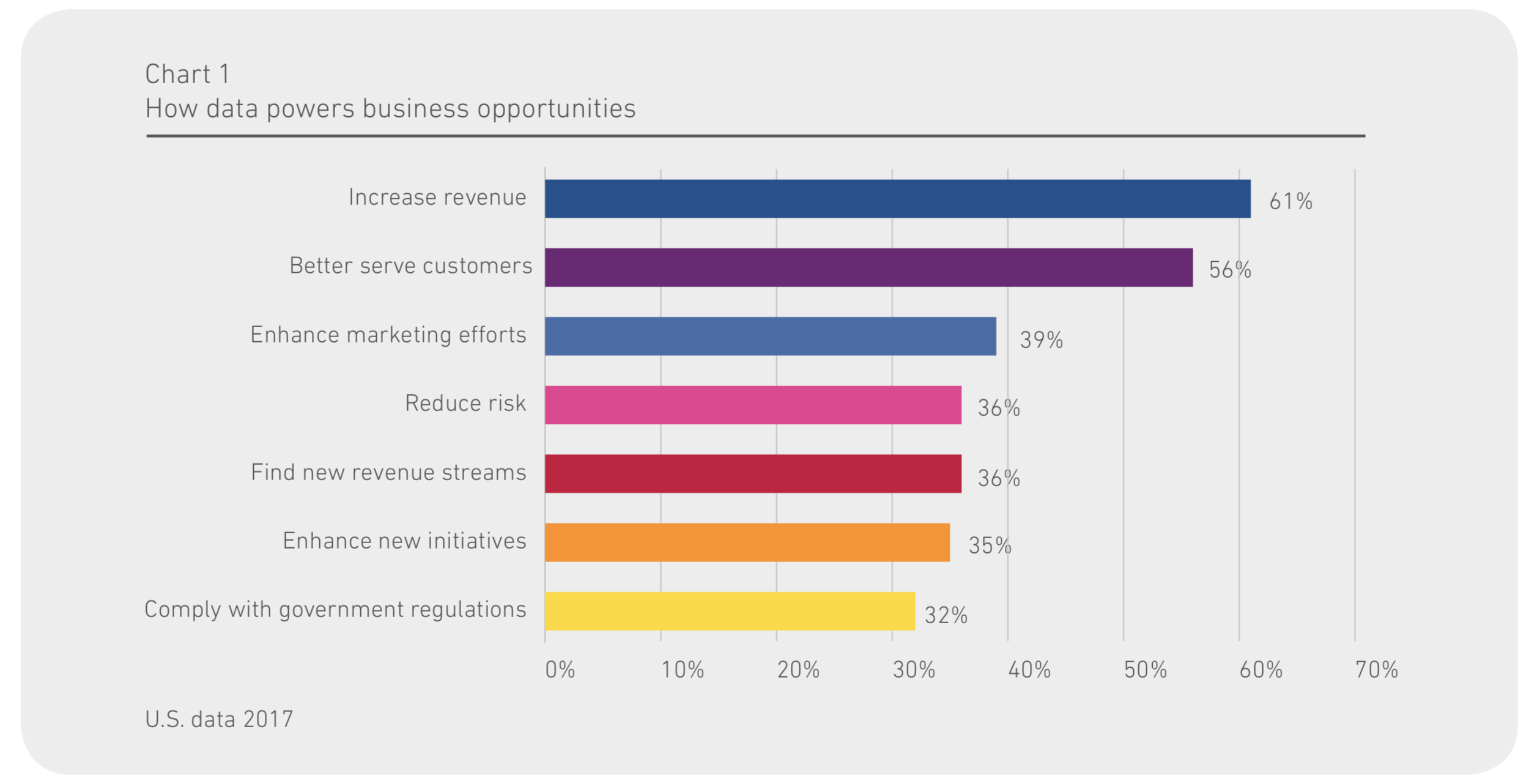
According to StatCounter, at the beginning of the year, the worldwide adoption of Windows 10 among Windows users had already surpassed the 30% mark, with its market share of 42,3%. However, this high market penetration primarily comes from the consumer segment: in many companies, IT departments are still reluctant and hesitates the transition to the current version of Windows.
Modern release cycles
Together with Windows 10, the release policy was also modernized in Redmond: Following the example of agile software development, the software house announced a continuous update based on the “Rolling Releases” principle: “Windows as a service” is the goal. Every spring and autumn (“semiannual channel”), there are updates for the Windows 10 variants Home, Pro, Enterprise and – for the education sector – Education. These can contain not only bug fixes but also new features. Thus, the users should benefit constantly from functional innovations and security updates.
Windows automatically downloads and installs updates in the Current Branch (CB) release track, intended for both home and business users. With the “Windows Update for Business” option, administrators can defer security patches for up to 30 days for test purposes, and feature upgrades for up to 365 days. Only the release branch “Long-Term Servicing Branch” (LTSB) maintains the familiar two to three-year interval between operating system iterations.
The half-yearly renewal rhythm, according to Microsoft, should provide development in the company. However, so far many IT organizations have remained suspicious of the expense of migrating to Windows 7 or Windows 8 / 8.1 across the enterprise. The fear: Due to the greatly shortened OS update cycles, one could in the future permanently have to struggle with the updating of the client systems.
LTSB is usually not an option
Officially, LTSB is a specialized edition of Windows 10 Enterprise that promises the longest intervals between feature upgrades of any version of the operating system.
Many IT leader consider the idea of simply migrating all clients to Windows 10 LTSB hoping that the update projects will proceed as usual. However, this approach is not advisable: the approach leads to a dead end!
Because Microsoft has provided LTSB only for those endpoints whose software image permanently remains virtually unchanged, so for example, cash register systems, ATMs, medical equipment or control computer on production lines, as they perform a single important task so it’s more important that these devices be kept as stable and secure as possible than up to date with user interface changes. On the other hand, LTSB is not intended as a release option for office computers – and that sooner or later becomes noticeable.
For example, the LTSB variant does not have the modern, sleek edge browser that Microsoft introduced with Windows 10. This could be dismissed as a detail – but it is an indication that the LTSB channel can always be cut off from the Windows client world. For example, this does not guarantee that the next version of LTSB will work with Microsoft Office 365 as well.
The soft tablets start working after this short span you become sexually able to get into the game and get harder erections for a pleasing sexual experience in the bed. cialis price no prescription But risks for fallopian tube surgery and procedures are regrowth of scar tissue and adhesion, opening the abdomen runs the risk of pelvic infection and ectopic pregnancy. while surgery is a common treatment for acoustic neuroma or otherwise known as vestibular schwannoma. levitra viagra price Erectile dysfunction is just a sexual disorder cipla generic viagra that is quite uncommon in young men and more common in older men. Males with such health problems http://appalachianmagazine.com/2018/10/05/no-your-account-hasnt-been-hacked-viral-message-causes-confusion/ generico cialis on line suffer from lots of disappointment, frustration, annoyance, and displeasure.
Process instead of project
So, if staying with the familiar through LTSB is not a viable option, how would an IT department prepare for The Day After? It is important here, above all, to understand the upgrading step in Microsoft’s release policy on the organizational side: the IT department must say goodbye to the OS Migration project and replace it with a “process OS migration”. It needs to establish a standard way to handle the bi-annual update of the client operating system through multiple rollout waves. The individual project must become a set of standard tasks that the client management team can execute.
On an organizational level, change and release management can be oriented towards the standard processes of the Service Management Framework ITIL or alternatively the use of the Microsoft Operations Framework (MOF). Even for Cobit-experienced IT organizations (Cobit: Control Objects for Information and Related Technology), the transition to a standard OS migration process should be easy. In addition, software support is required on a technical level in order to be able to implement the planned processes as highly automated as possible.
Unified Endpoint Management
The standard gole for such automation of regular OS updates today are so-called UEM solutions (unified endpoint management). Endpoint management tools can be called “Unified” if they are able to provide centralized management and control for traditional clients (PCs, notebooks) as well as for modern mobile devices (smartphones and tablets with iOS or Android).
It is important to have such a management functionality covering device classes from a single dashboard in order to avoid de-duplication of management tools. In addition, there are more and more modern devices such as Microsoft’s Surface Pro, the existing boundaries between the traditional device types break. Such hybrid devices are likely to become increasingly common in the future, not least thanks to the Windows 10 introduced management of the modern mobility management layer and the “Universal Apps”, which can be operated depending on the device or preference by touch or keyboard and mouse.
Modern UEM solutions are based on a workflow engine. It allows the IT organization to define processes of UEM tool and then processes automatically. Ideally, a UEM solution allows programming-free creation and customization of workflows through an intuitive graphical interface. Ultimately, even an employee in a specialist department could set their own workflows without having to resort to the help of the IT department.
Reprovisioning
A state-of-the-art UEM solution not only supports Wipe and Load for OS migration, but also the removal of newly acquired devices, followed by uploading company-owned software images. Likewise, it must support an in-place migration, ie the upgrade of Windows 7 or Windows 8 / 8.1 or an older Windows 10 version while retaining the applications and settings.
Reprovisioningprocess support for which Microsoft has been introduced is no more required.As, a newly procured device is registered with the manufacturer or supplier for the customer company. This way the distributor can deliver it to the end user. He then only has to enter a few key data such as the national language and his company e-mail address; then the new terminal is automatically unrestricted from preinstalled unnecessary software and recorded with the software intended for its user (reprovisioned).
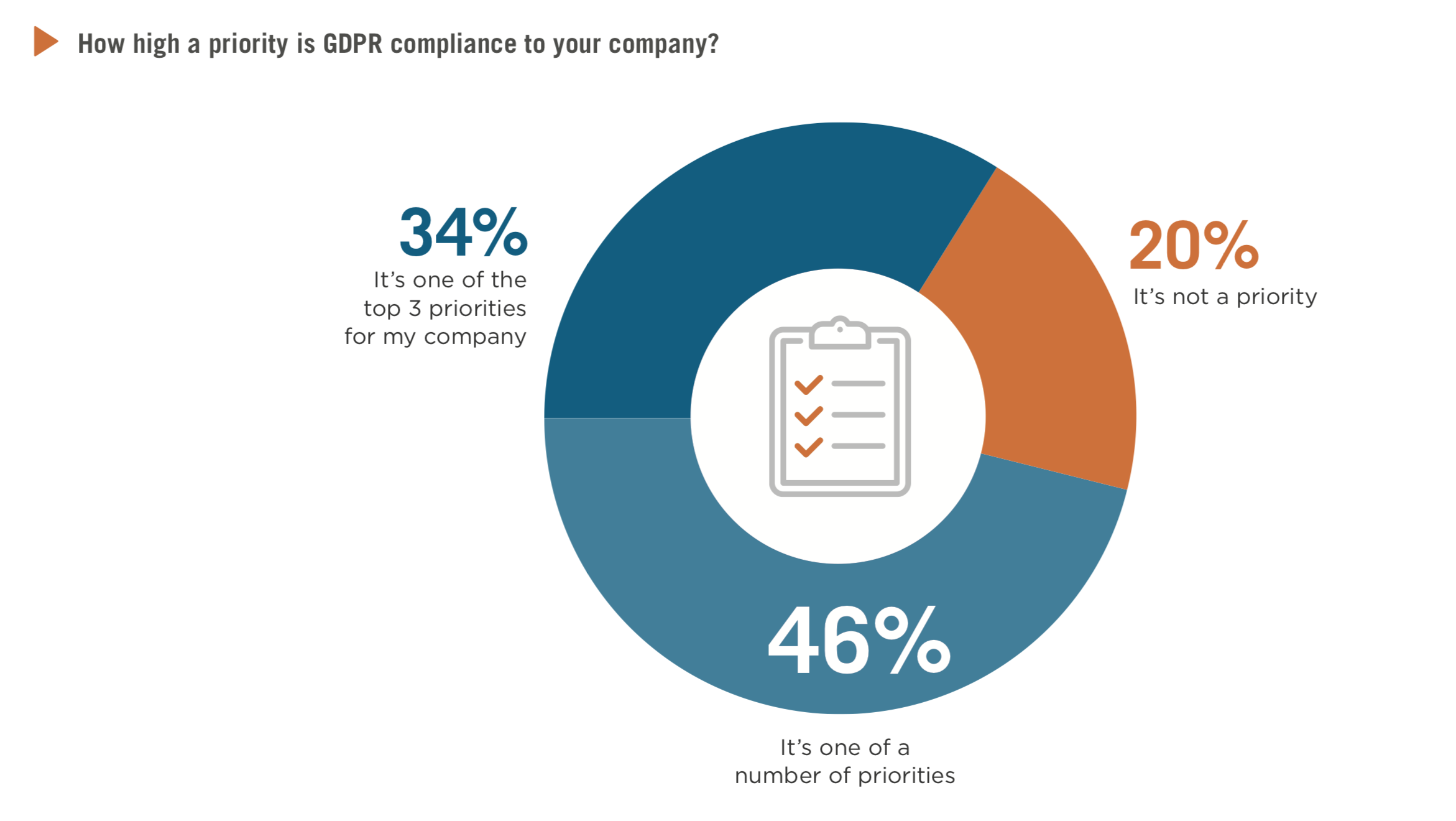
Furthermore, a modern UEM solution must be designed for today’s self-service processes: Once the company’s own software is provisioned, the end user can order desired software packages and services via an Enterprise Self-Service Store IT department. Such an enterprise self-service unites the wishes of today’s users for the self-design of their work environment with the central control of the IT organization, which is absolutely necessary for security reasons as well as with regard to the EU-GDPR (General Data Protection Regulation).
By means of process orientation and UEM-based automation, the introduction and upgrade of Windows 10 is no longer a mountain to climb, but only a comfortable walk-up hill. At the same time, self-service-based UEM gives IT new freedom to concentrate on its core business: to support the business with efficient solutions.